An analyst is investigating how an attacker successfully performs a brute-force attack to gain a foothold into an organizations systems. In the course of the investigation the analyst determines that the reason no alerts were generated is because the detection searches were configured to run against Windows data only and excluding any Linux data.
This is an example of what?
Correct Answer:
C
This scenario is an example of aFalse Negativebecause the detection mechanisms failed to generate alerts for a brute-force attack due to a misconfiguration—specifically, the exclusion of Linux data from the detection searches. A False Negative occurs when a security control fails to detect an actual malicious activity that it is supposed to catch, leading to undetected attacks and potential breaches.
An analyst is building a search to examine Windows XML Event Logs, but the initial search is not returning any extracted fields. Based on the above image, what is themost likelycause?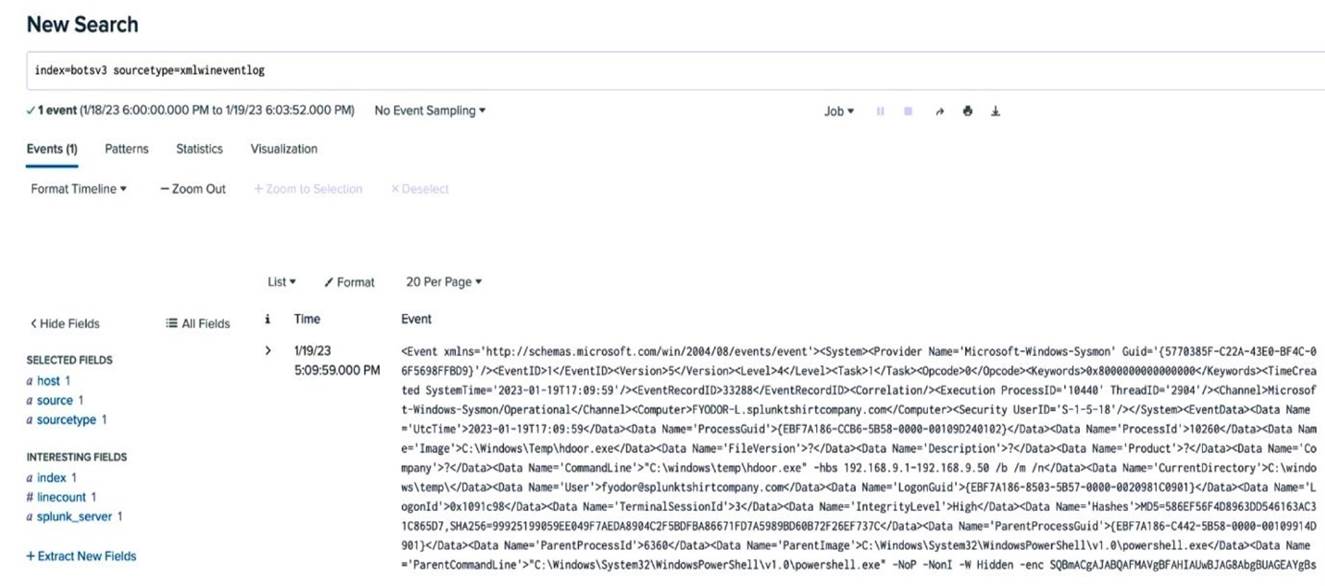
Correct Answer:
D
In Splunk, when an analyst is building a search and finds that extracted fields are not appearing, it often relates to the search mode being used.Smart ModeorVerbose Modeare better suitedfor field extraction as they allow Splunk to automatically extract and display fields based on the data being searched.
✑ Search Modes in Splunk:
✑ Incorrect Options:
✑ Splunk Documentation:Search modes and their impact on field extraction.
An analyst needs to create a new field at search time. Which Splunk command will dynamically extract additional fields as part of a Search pipeline?
Correct Answer:
A
In Splunk, therexcommand is used to extract fields from raw event data using regular expressions. This command allows analysts to dynamically extract additional fields as part of a search pipeline, which is crucial for creating new fields during search time based on specific patterns found in the log data. Therexcommand is highly flexible and powerful, making it essential for refining and manipulating data in a Splunk environment. The other options (fields,regex,eval) have their uses, butrexis specifically designed for dynamic field extraction.
Which of the following is not considered an Indicator of Compromise (IOC)?
Correct Answer:
D
Indicators of Compromise (IOCs) are artifacts that are used to identify potential malicious activity within a network or system. Common IOCs include domains, IP addresses, and file hashes that are associated with malicious activity. However, a specific password, while potentially sensitive, is not typically considered an IOC because it is more of a credential than an artifact indicating a compromise. IOCs are used to detect and respond to threats, while compromised credentials are a result of those threats.
An analyst is attempting to investigate a Notable Event within Enterprise Security. Through the course of their investigation they determined that the logs and artifacts needed to investigate the alert are not available.
What event disposition should the analyst assign to the Notable Event?
Correct Answer:
D
In this scenario, the analyst cannot conclude whether the Notable Event is a true positive or a false positive due to the absence of necessary logs and artifacts. The appropriate eventdisposition in this case is "Other," as it indicates that further action is required, such as ingesting the missing logs. The involvement of a security engineer to ensure the necessary data is available for proper investigation is implied, making "Other" the most suitable option.