- (Exam Topic 4)
You have a Microsoft 365 tenant.
You need to Identity users who have leaked credentials. The solution must meet the following requirements:
• Identity sign-ms by users who are suspected of having leaked credentials.
• Flag the sign-ins as a high-risk event.
• Immediately enforce a control to mitigate the risk, while still allowing the user to access applications. What should you use? To answer, select the appropriate options m the answer area.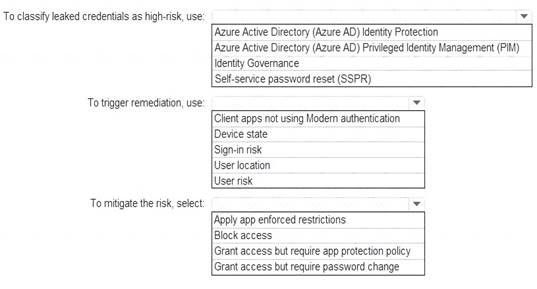
Solution: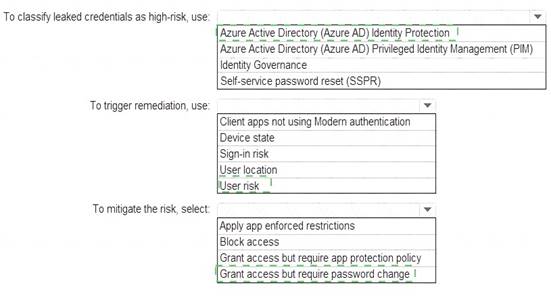
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have an Azure subscription.
Azure AD logs are sent to a Log Analytics workspace.
You need to query the logs and graphically display the number of sign-ins per user.
How should you complete the query? To answer, select the appropriate options in the answer area.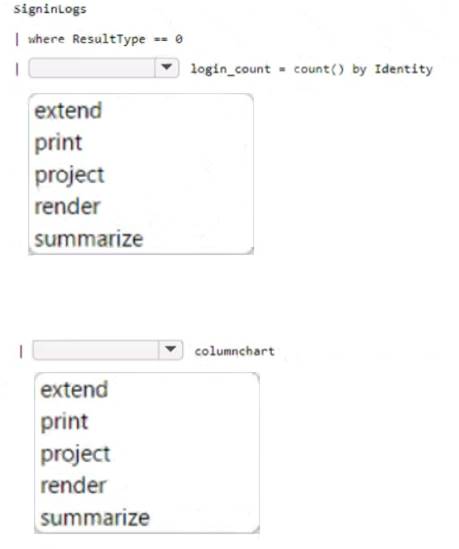
Solution:
Box 1 = SigninLogs
| where ResultType == 0
| summarize login_count = count() by identity
| render piechart
This query retrieves the sign-in logs, filters the successful sign-ins, summarizes the count of sign-ins per user, and renders the result as a pie chart.
Box 2 = Render
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have a Microsoft 365 tenant.
You need to identify users who have leaked credentials. The solution must meet the following requirements.
• Identity sign-Ins by users who ate suspected of having leaked credentials.
• Rag the sign-ins as a high risk event.
• Immediately enforce a control to mitigate the risk, while still allowing the user to access applications. What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Solution:
Graphical user interface, text, application, email Description automatically generated
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure password writeback. Does this meet the goal?
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
- (Exam Topic 4)
You have an Azure AD tenant
You open the risk detections report.
Which risk detection type is classified as a user risk?
Correct Answer:
A