Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall’s data plane?
Correct Answer:
B
Which component is a building block in a Security policy rule?
Correct Answer:
D
Reference:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/policies/policies-security/buildingblocks-in-a-security-policy-rule.html
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
Correct Answer:
D
If users from the Trusted zone need to allow traffic to an SFTP server in the DMZ zone, how should a Security policy with App-ID be configured? A)
A)
B)
C)
D)
Correct Answer:
D
Given the screenshot what two types of route is the administrator configuring? (Choose two)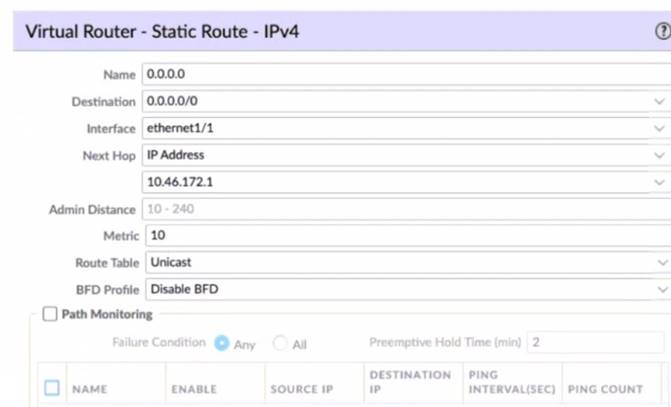
Correct Answer:
A