Based on the security policy rules shown, ssh will be allowed on which port?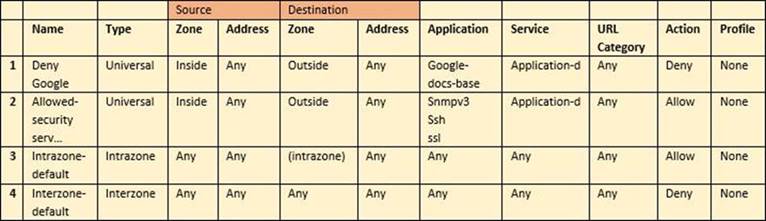
Correct Answer:
C
Which administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact and command-and-control (C2) server.
Which security profile components will detect and prevent this threat after the firewall`s signature database has been updated?
Correct Answer:
C
Based on the graphic, what is the purpose of the SSL/TLS Service profile configuration option?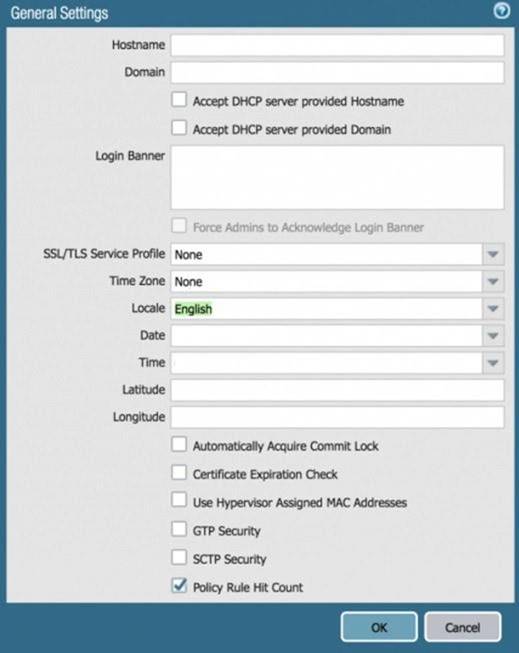
Correct Answer:
C
What is considered best practice with regards to committing configuration changes?
Correct Answer:
A
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
Correct Answer:
C