An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?
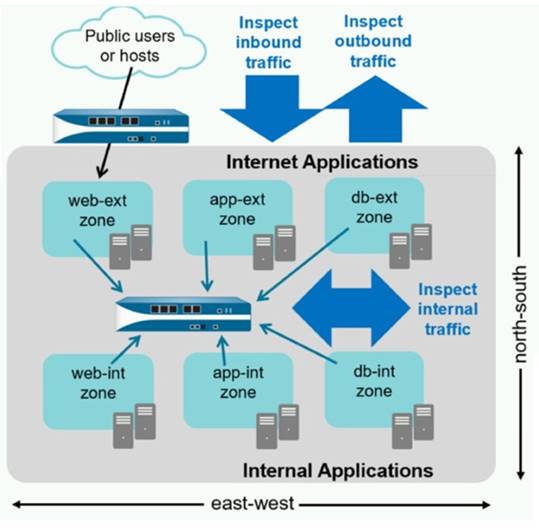
Correct Answer:
D
What are three valid ways to map an IP address to a username? (Choose three.)
Correct Answer:
ACD
Which five Zero Trust concepts does a Palo Alto Networks firewall apply to achieve an integrated approach to prevent threats? (Choose five.)
Correct Answer:
ACDEF
 Which plane on a Palo alto networks firewall provides configuration logging and reporting functions on a separate processor?
Which plane on a Palo alto networks firewall provides configuration logging and reporting functions on a separate processor?
Correct Answer:
C
Which object would an administrator create to enable access to all applications in the office-programs subcategory?
Correct Answer:
C