A native hypervisor runs:
Correct Answer:
D
Type 1 (native or bare metal). Runs directly on the host computer’s hardware Type 2 (hosted). Runs within an operating system environment
Match the Identity and Access Management (IAM) security control with the appropriate definition.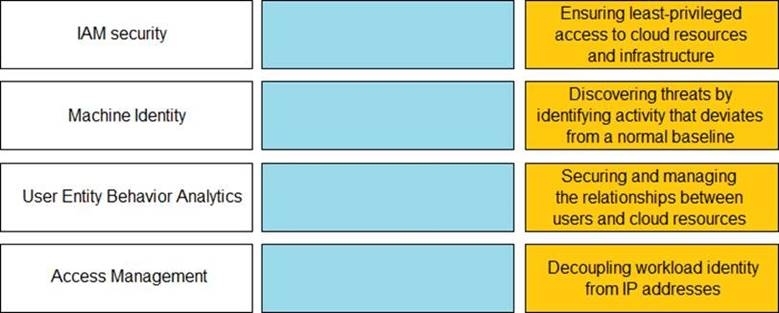
Solution: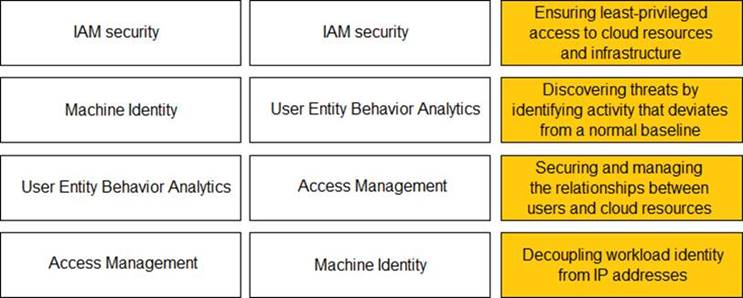
Does this meet the goal?
Correct Answer:
A
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
Correct Answer:
A
In anti-malware, a false positive incorrectly identifies a legitimate file or application as malware. A false negative incorrectly identifies malware as a legitimate file or application. In intrusion detection, a false positive incorrectly identifies legitimate traffic as a threat, and a false negative incorrectly identifies a threat as legitimate traffic.
Which type of LAN technology is being displayed in the diagram?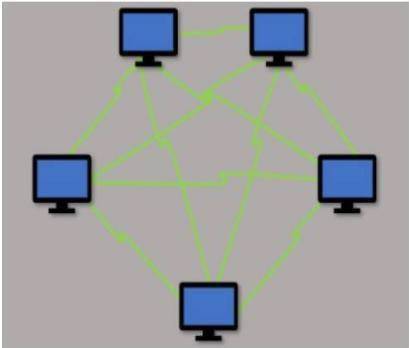
Correct Answer:
A
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
Correct Answer:
D