In the attached network diagram, which device is the switch?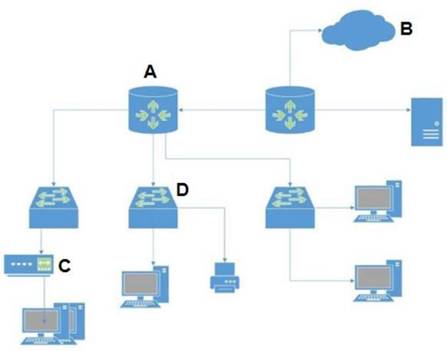
Correct Answer:
D
Match the Palo Alto Networks WildFire analysis verdict with its definition.
Solution:
Benign: Safe and does not exhibit malicious behavior
Grayware: No security risk but might display obtrusive behavior (for example, adware, spyware, and browser helper objects)
Malware: Malicious in nature and intent and can pose a security threat (for example, viruses, worms, trojans, root kits, botnets, and remote-access toolkits)
Phishing: Malicious attempt to trick the recipient into revealing sensitive data
Does this meet the goal?
Correct Answer:
A
In a traditional data center what is one result of sequential traffic analysis?
Correct Answer:
C
Multiple policies, no policy reconciliation tools: Sequential traffic analysis (stateful inspection, application control, intrusion prevention system (IPS), anti-malware, etc.) in traditional data center security solutions requires a corresponding security policy or profile, often using multiple management tools. The result is that your security policies become convoluted as you build and manage a firewall policy with source, destination, user, port, and action; an application control policy with similar rules; and any other threat prevention rules required. Multiple security policies that mix positive (firewall) and negative (application control, IPS, and anti-malware) control models can cause security holes by missing traffic and/or not identifying
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
Correct Answer:
D
Prisma SaaS connects directly to the applications themselves, therefore providing continuous silent monitoring of the risks within the sanctioned SaaS applications, with detailed visibility that is not possible with traditional security solutions.
Match the description with the VPN technology.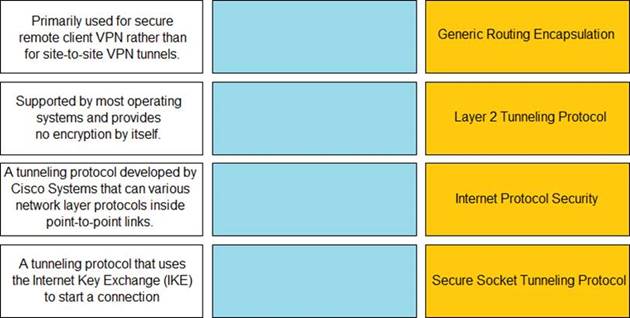
Solution: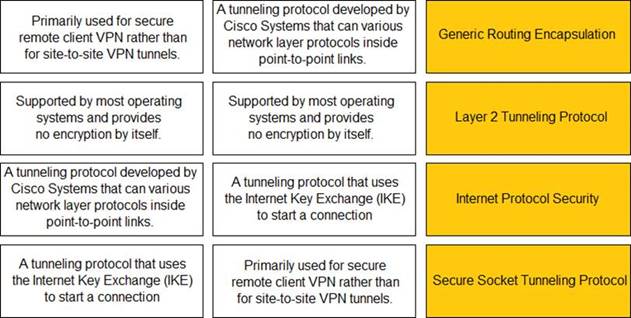
Does this meet the goal?
Correct Answer:
A