When the CPM connects to a database, which interface is most commonly used?
Correct Answer:
B
The Central Policy Manager (CPM) in CyberArk most commonly uses the ODBC (Open Database Connectivity) interface when connecting to a database. ODBC is a standard API for accessing database management systems (DBMS). The CPM supports remote password management on all databases that support ODBC connections, and the machine running the CPM must support ODBC, version 2.7 and higher1. References:
✑ CyberArk Docs: Databases that support ODBC connections1
DRAG DROP
Match each PTA alert category with the PTA sensors that collect the data for it.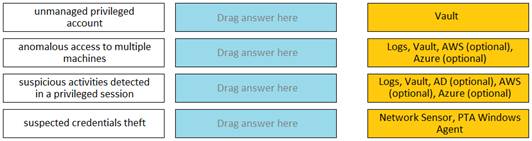
Solution:
Comprehensive Explanation: The Privileged Threat Analytics (PTA) sensors are designed to collect specific types of data to detect potential security threats. For the alert category of Unmanaged privileged account, the Network Sensor andPTA Windows Agent are responsible for collecting the relevant data. Similarly, for the alert category of Anomalous access to multiple machines, data is collected from Logs, the Vault, and optionally from AWS andAzure. The Suspicious activities detected in a privileged session category relies on data fromLogs, the Vault, and optionally from AD, AWS, and Azure. Lastly, the Suspected credentials theft category also utilizes theNetwork Sensor andPTA Windows Agent for data collection.
References:
✑ CyberArk’s official training materials and documentation provide detailed information on PTA sensors and the types of data they collect for different alert categories.
Does this meet the goal?
Correct Answer:
A
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
Correct Answer:
C
To add an LDAP group to a CyberArk group, you need to use the Private Ark client and follow these steps1:
✑ In the Users and Groups tree, select the CyberArk group that you want to add the
LDAP group to.
✑ In the Properties pane, click Member Of.
✑ Click Add > LDAP Group.
✑ In the LDAP Group dialog box, enter the name of the LDAP group and click OK. References: Add an LDAP group to a Vault group
Which accounts can be selected for use in the Windows discovery process? (Choose two.)
Correct Answer:
AB
During the Windows discovery process in CyberArk Defender PAM, accounts that can be selected for use include an account that is already stored in the Vault and an account that is specified by the user. The discovery process scans predefined machines for new and modified accounts and their dependencies. After the scan, accounts that should be onboarded into the Vault for secure and automatic management are identified12. References: The information provided is based on general knowledge of CyberArk PAM best practices and the account discovery process as outlined in CyberArk’s official documentation1
One can create exceptions to the Master Policy based on .
Correct Answer:
B
The Master Policy is a set of rules that apply to all accounts in the Vault. However, one can create exceptions to the Master Policy based on platforms, which are logical groupings of accounts that share common characteristics, such as operating system, device type, or application. By creating platform-specific policies, one can override the Master Policy settings for certain accounts and customize the security and management options for different platforms. References:
✑ Defender PAM Sample Items Study Guide, page 9
✑ CyberArk Core Privileged Access Security Documentation, Master Policy Overview and Platform-Specific Policies