Refer to Exhibit: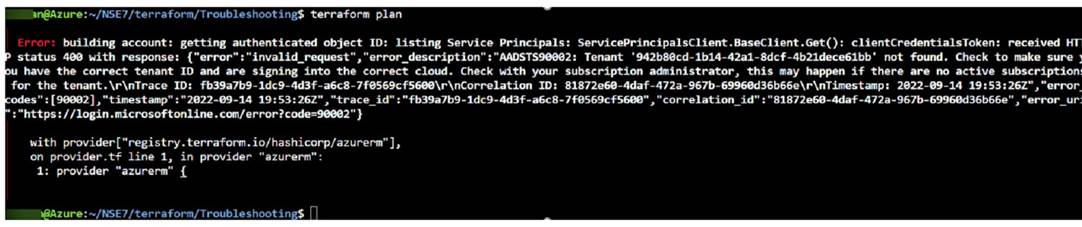
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run Which two statements about running the plan command are true? (Choose two.)
Correct Answer:
CD
✑ A is incorrect because the terraform plan command will not deploy any resources at all. It will only show the changes that would be made if the terraform apply command was run. The error message in the exhibit indicates that the service principal details are invalid, which means that Terraform cannot authenticate to Azure and cannot create any resources1.
✑ B is incorrect because you can run the terraform apply command without running the terraform plan command first. The terraform apply command will automatically generate a new plan and prompt you to approve it before applying it2. However, running the terraform plan command first can help you preview the changes and avoid any unwanted or unexpected actions.
✑ C is correct because you must run the terraform init command once before the terraform plan command. The terraform init command initializes a working
directory containing Terraform configuration files. It downloads and installs the provider plugins required for your configuration, such as the Azure provider2. It also creates a hidden directory called .terraform to store the plugin binaries and other metadata1. Without running the terraform init command, the terraform plan command will fail because it cannot find the required plugins or modules.
✑ D is correct because the terraform plan command makes Terraform do a dry run.
A dry run is a simulation of what would happen if you executed a certain action, without actually performing it. The terraform plan command creates an execution plan, which is a description of the actions that Terraform would take to make your infrastructure match your configuration2. The execution plan shows you what resources will be created, modified, or destroyed, and what attributes will be changed. The execution plan does not affect your infrastructure or state file until you apply it with the terraform apply command1.
How does an administrator secure container environments from newly emerged security threats?
Correct Answer:
D
Securing container environments from newly emerged security threats involves employing specific security mechanisms tailored to the technology and structure of containers. In this context, the use of Docker-related application control signatures (Option D) is critical for effectively managing and mitigating threats in containerized environments.
✑ Docker-Specific Threats:Docker containers, being a prevalent form of container technology, are targeted by various security threats, including those that exploit vulnerabilities specific to the Docker environment and runtime. Using Docker- related application control signatures means implementing security measures that are specifically designed to detect and respond to anomalies and threats that are unique to Docker containers.
✑ Application Control Signatures:These are sets of definitions that help identify and block potentially malicious activities within application traffic. By focusing on Docker-related signatures, administrators can ensure that the security tools are finely tuned to the operational specifics of Docker containers, thereby providing a robust defense against exploits that target container-specific vulnerabilities.
References:The recommendation to use Docker-related application control signatures is based on best practices for securing container environments, emphasizing the need for specialized security measures that address the unique challenges posed by container technologies.
What are three important steps required to get Terraform ready using Microsoft Azure Cloud Shell? (Choose three.)
Correct Answer:
ADE
To get Terraform ready using Microsoft Azure Cloud Shell, you need to perform the following steps:
✑ Set up a storage account in Azure. This is required to store the Terraform state file in a blob container, which enables collaboration and persistence of the infrastructure configuration1.
✑ Use the wget (terraform_version) command to upload Terraform. This command downloads the latest version of Terraform from the official website and saves it as a zip file in the current directory2.
✑ Move the Terraform file to the bin directory. This step extracts the Terraform executable from the zip file and moves it to the bin directory, which is part of the PATH environment variable. This allows you to run Terraform commands from any directory in Cloud Shell2.
The other options are incorrect because:
✑ You do not need to use the -O command to download Terraform. This command is used to specify a different output file name for the downloaded file, but it is not necessary for this task3.
✑ You do not need to subscribe to Terraform in Azure. Terraform is an open-source tool that can be used with any cloud provider, and there is no subscription or registration required to use it with Azure4. References:
✑ Updating the route table and adding an IAM policy
✑ Configure Terraform in Azure Cloud Shell with Bash
✑ wget(1) - Linux man page
✑ Terraform by HashiCorp
Refer to the exhibit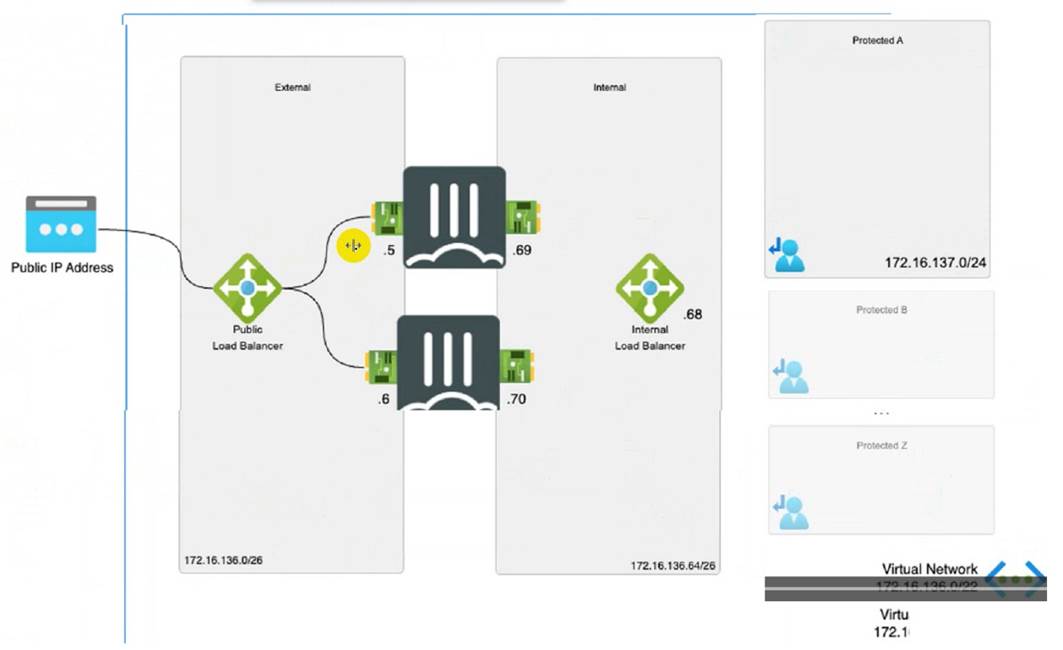
Consider the active-active load balance sandwich scenario in Microsoft Azure.
What are two important facts in the active-active load balance sandwich scenario? (Choose two )
Correct Answer:
BD
* B. It is recommended to enable NAT on FortiGate policies. This is because the Azure load balancer uses a hash-based algorithm to distribute traffic to the FortiGate instances, and it relies on the source and destination IP addresses and ports of the packets1. If NAT is not enabled, the source IP address of the packets will be the same as the load balancer??s frontend IP address, which will result in uneven distribution of traffic and possible asymmetric routing issues1. Therefore, it is recommended to enable NAT on the FortiGate policies to preserve the original source IP address of the packets and ensure optimal load balancing and routing1. D. It supports session synchronization for handling asynchronous traffic. This means that the FortiGate instances can synchronize their session tables with each other, so that they can handle traffic that does not follow the same path as the initial packet of a session2. For example, if a TCP SYN packet is sent to FortiGate A, but the TCP SYN-ACK packet is sent to FortiGate B, FortiGate B can forward the packet to FortiGate A by looking up the session table2. This feature allows the FortiGate instances to handle asymmetric traffic that may occur due to the Azure load balancer??s hash-based algorithm or other factors.
The other options are incorrect because:
✑ It does not use the vdom-exception command to exclude the configuration from being synced. The vdom-exception command is used to exclude certain configuration settings from being synchronized between FortiGate devices in a cluster or a high availability group3. However, in this scenario, the FortiGate devices are not in a cluster or a high availability group, but they are standalone devices with standalone configuration synchronization enabled. This feature allows them to synchronize most of their configuration settings with each other, except for some settings that identify the FortiGate to the network, such as the hostname.
✑ It does not use the FGCP protocol. FGCP stands for FortiGate Clustering Protocol, which is used to synchronize configuration and state information between FortiGate devices in a cluster or a high availability group. However, in this scenario, the FortiGate devices are not in a cluster or a high availability group, and they use standalone configuration synchronization instead of FGCP.
Refer to the exhibit.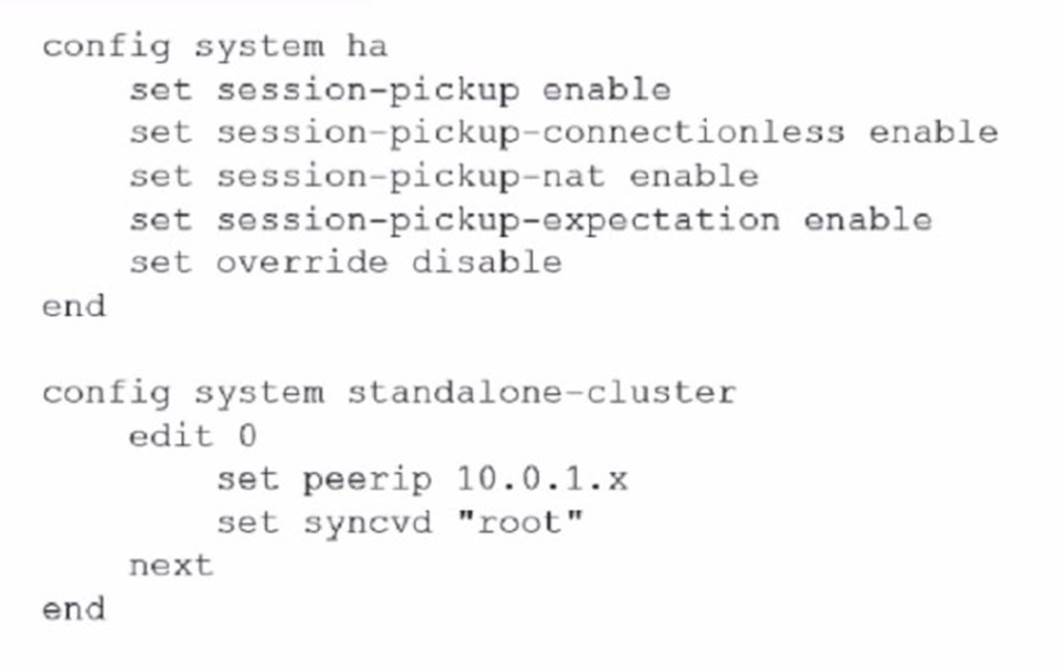
You deployed an HA active-active load balance sandwich with two FortiGate VMs in Microsoft Azure.
After the deployment, you prefer to use FGSP to synchronize sessions, and allowasymmetric return traffic In the environment, FortiGate port 1 and port 2 are facing external and internal load balancers respectively
What IP address must you use in the peerip configuration?
Correct Answer:
D
In an HA active-active load balance configuration with FortiGate VMs, especially in Microsoft Azure where FGSP (FortiGate Session Life Support Protocol) is used for session synchronization, the correct configuration for thepeeripis: D.The opposite FortiGate port 2 IP address.
✑ HA Synchronization Requirements:FGSP requires direct communication between the FortiGates to synchronize the session table. This synchronization typically occurs over a dedicated HA link that connects the HA pair.
✑ Asymmetric Traffic Considerations:FGSP allows asymmetric traffic to rejoin the correct session by synchronizing session information, including NAT and TCP sequence tracking between the FortiGate units in a cluster.
✑ Configuration Specifics:For port 2, which is facing the internal load balancer, thepeeripshould be set to the corresponding port 2 IP address of the opposite FortiGate. This allows the internal interfaces to communicate directly with each other for session synchronization purposes, which is crucial in an active-active deployment to ensure sessions persist during failover scenarios. References:The choice of using port 2's IP address for FGSP is supported by the Fortinet documentation, which explains how FortiGates should be configured for HA, especially in cloud environments where traditional HA links may not be available.