- (Exam Topic 4)
You have a Microsoft 365 subscription that contains the users shown in the following table.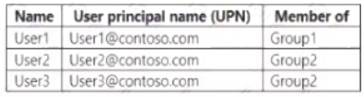
Group1 is member of a group named Group3.
The Azure Active Directory (Azure AD) tenant contains the Windows 10 devices shown in the following table.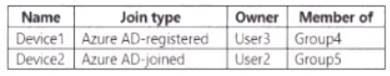
Microsoft Endpoint Manager has the devices shown in the following table.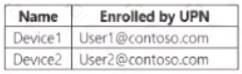
Microsoft Endpoint Manager contains the compliance policies shown in the following table.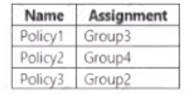
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Solution:
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
Several users in your Microsoft 365 subscription report that they received an email message without the attachment. You need to review the attachments that were removed from the messages. Which two tools can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Correct Answer:
AD
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/manage-quarantined-messages-and-files
- (Exam Topic 4)
You have a Microsoft 365 subscription.
A user reports that changes were made to several files in Microsoft OneDrive.
You need to identify which files were modified by which users in the user’s OneDrive. What should you do?
Correct Answer:
D
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/activity-filters
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1. For User1, you select Confirm user compromised.
User1 can still sign in.
You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the sign-in risk policy to block access when the sign-in risk level is high. Does this meet the goal?
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-investigate
- (Exam Topic 4)
You have a Microsoft 365 E5 subscription.
You implement Advanced Threat Protection (ATP) safe attachments policies for all users.
User reports that email messages containing attachments take longer than expected to be received.
You need to reduce the amount of time it takes to receive email messages that contain attachments. The solution must ensure that all attachments are scanned for malware. Attachments that have malware must be blocked.
What should you do from ATP?
Correct Answer:
D
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/dynamic-delivery-and-previewing