- (Topic 6)
Your network contains an Active Directory domain named adatum.com that is synced to Azure AD.
The domain contains 100 user accounts.
The city attribute for all the users is set to the city where the user resides.
You need to modify the value of the city attribute to the three-letter airport code of each city.
What should you do?
Correct Answer:
A
The user accounts are synced from the on-premise Active Directory to the Microsoft Azure Active Directory (Azure AD). Therefore, the city attribute must be changed in the on- premise Active Directory.
You can use Windows PowerShell on a domain controller and run the Get-ADUser cmdlet to get the required users and pipe the results into Set-ADUser cmdlet to modify the city attribute.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
* 1. From Windows PowerShell on a domain controller, run the Get-ADUser and Set-ADUser cmdlets.
* 2. From Active Directory Administrative Center, select the Active Directory users, and then modify the Properties settings.
Other incorrect answer options you may see on the exam include the following:
* 1. From the Azure portal, select all the Azure AD users, and then use the User settings blade.
* 2. From Windows PowerShell on a domain controller, run the Get-AzureADUser and Set- AzureADUser cmdlets.
* 3. From the Microsoft 365 admin center, select the users, and then use the Bulk actions option.
* 4. From Azure Cloud Shell, run the Get-ADUser and Set-ADUser cmdlets.
Reference:
https://docs.microsoft.com/en-us/powershell/module/addsadministration/set-aduser
DRAG DROP - (Topic 6)
You have a Microsoft 365 subscription.
You need to review reports to identify the following:
• The storage usage of files stored in Microsoft Teams
• The number of active users per team
Which report should you review for each requirement? To answer, drag the appropriate reports to the correct requirements. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content
Solution:
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 6)
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.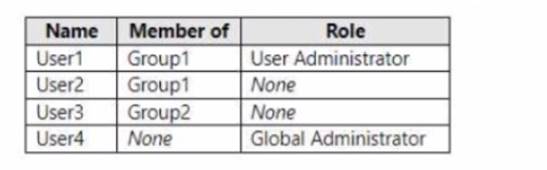
You enable self-service password reset (SSPR) for Group1. You configure security questions as the only authentication method for SSPR.
Which users can use SSPR, and which users must answer security questions to reset their password? To answer, select the appropriate options in the answer area.
NOTE; Each correct selection is worth one point.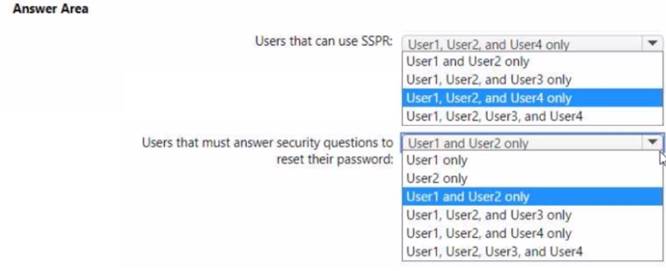
Solution: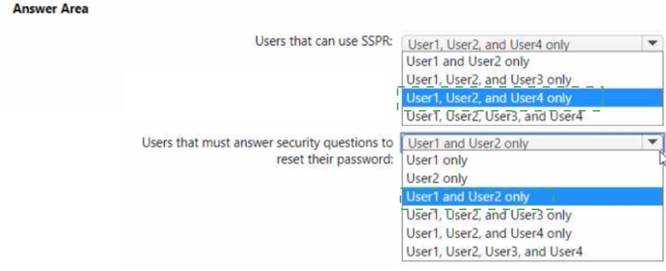
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 6)
You configure a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.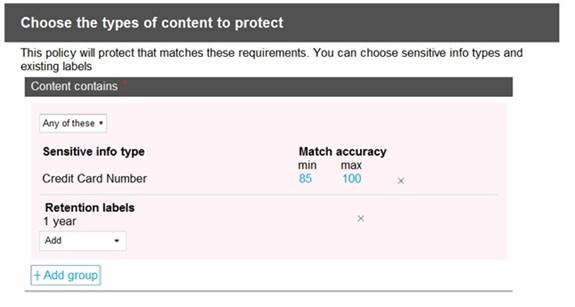
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.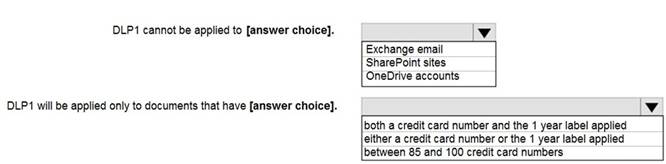
Solution:
Using a retention label in a policy is only supported for items in SharePoint Online and OneDrive for Business.
Does this meet the goal?
Correct Answer:
A
- (Topic 6)
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User1. you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
Correct Answer:
D