- (Exam Topic 4)
You have a Microsoft 365 E5 tenant.
You have a sensitivity label configured as shown in the Sensitivity label exhibit. (Click the Sensitivity label
tab.)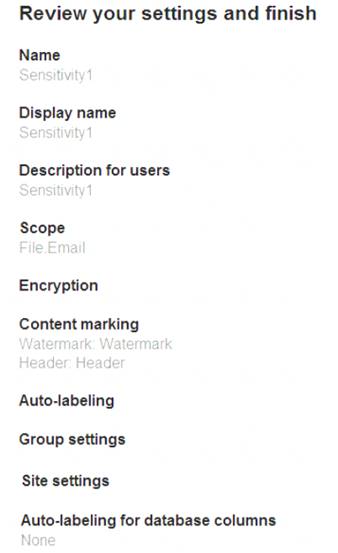
You have an auto-labeling policy as shown in the Auto-labeling policy exhibit. (Click the Auto-labeling policy tab.)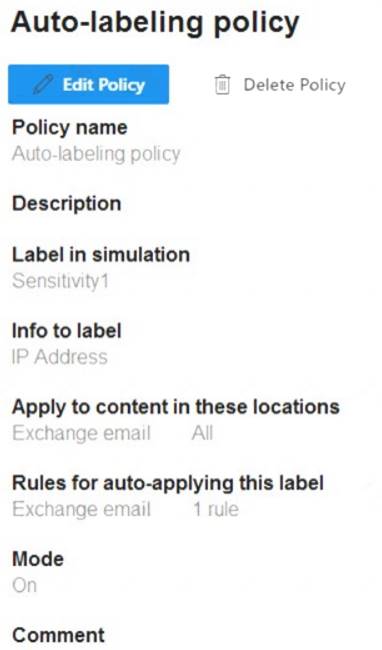
A user sends an email that contains the components shown in the following table.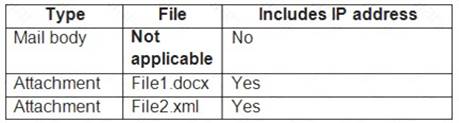
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.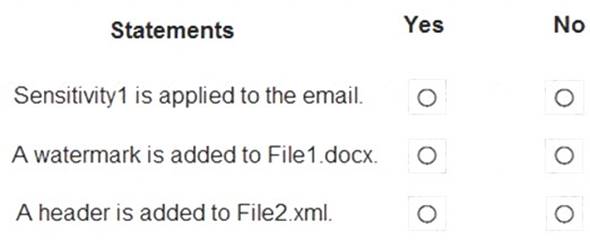
Solution:
Graphical user interface, text, application Description automatically generated
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-w
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 1)
You need to configure a conditional access policy to meet the compliance requirements. You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.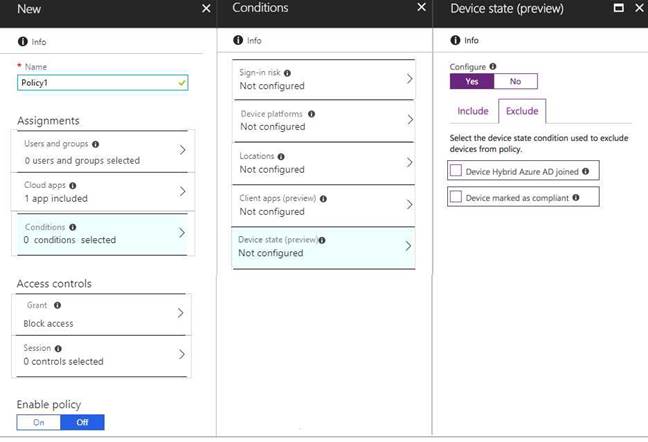
Solution:
Suggested Answer
References:https://docs.microsoft.com/en-us/intune/create-conditional-access-intune
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have a Microsoft 365 E5 subscription.
You configure a new alert policy as shown in the following exhibit.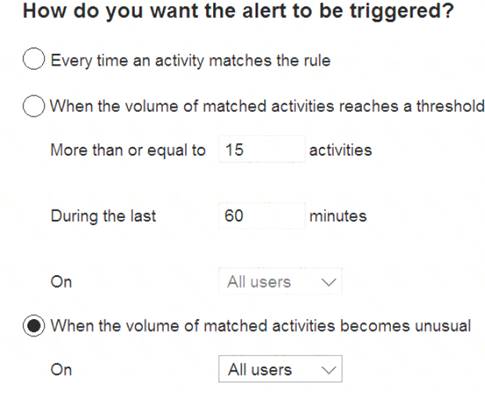
You need to identify the following: How many days it will take to establish a baseline for unusual activity.
How many days it will take to establish a baseline for unusual activity.  Whether alerts will be triggered during the establishment of the baseline.
Whether alerts will be triggered during the establishment of the baseline.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.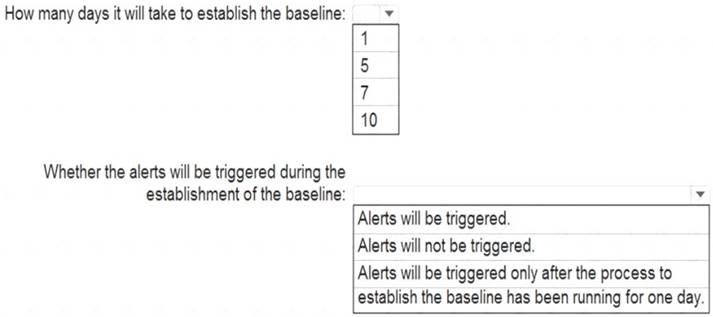
Solution:
Graphical user interface, text, application Description automatically generated
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have a Microsoft 365 subscription that contains the users shown in the following table.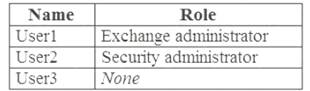
You run the following cmdlet.
Set-MailboxAuditBypassAssociation –Identity User2
–AuditByPassEnabled $true
The users perform the following actions: User1 accesses an item in the mailbox of User2.
User1 accesses an item in the mailbox of User2. User2 modifies a mailbox item in the mailbox of User3.
User2 modifies a mailbox item in the mailbox of User3.  User3 signs in to her mailbox.
User3 signs in to her mailbox.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.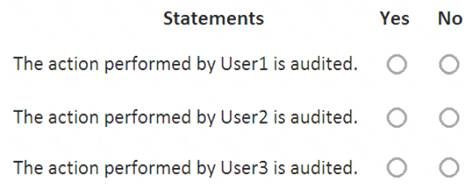
Solution:
Reference:
https://docs.microsoft.com/en-us/powershell/module/exchange/set-mailboxauditbypassassociation?view=exchan
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You deploy Microsoft Azure Information Protection.
You need to ensure that a security administrator named SecAdmin1 can always read and inspect data protected by Azure Rights Management (Azure RMS).
What should you do?
Correct Answer:
D
References:
https://docs.microsoft.com/en-us/azure/information-protection/configure-super-users