- (Exam Topic 4)
You are a network administrator at your company.
A user attempts to start a computer and receives the following error message: “Bootmgr is missing.” You need to resolve the issue.
You start the computer in the recovery mode.
Which command should you run next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.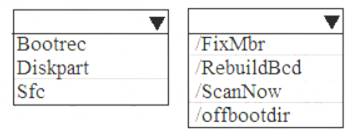
Solution:
References: https://neosmart.net/wiki/bootmgr-is-missing/
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have a Microsoft 365 Enterprise E3 license.
You have a computer named Computer1 that runs Windows 10.
You need to ensure that you can access the files on Computer1 by using a web browser on another computer. What should you configure?
Correct Answer:
C
- (Exam Topic 2)
You need to meet the technical requirements for the San Diego office computers. Which Windows 10 deployment method should you use?
Correct Answer:
B
References:
https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/windows-autopilot
- (Exam Topic 4)
Your network contains an Active Directory forest. The forest contains a root domain named contoso.com and a child domain named corp.contoso.com.
You have a computer named Computer1 that runs Windows 10. Computer1 is joined to the corp.contoso.com domain.
Computer1 contains a folder named Folder1. In the Security settings of Folder1, Everyone is assigned the Full control permissions.
On Computer1, you share Folder1 as Share1 and assign the Read permissions for Share1 to the Users group. For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.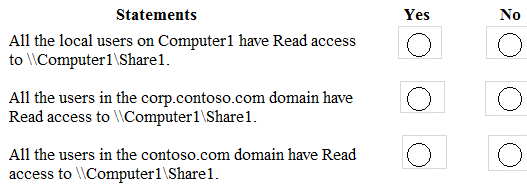
Solution:
References:
https://www.techrepublic.com/article/learn-the-basic-differences-between-share-and-ntfs-permissions/
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The computers contain the local security principals shown in the following table.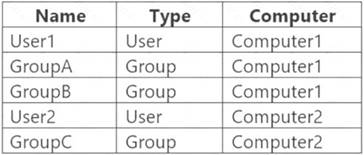
Which security principals can be members of GroupA and GroupC? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.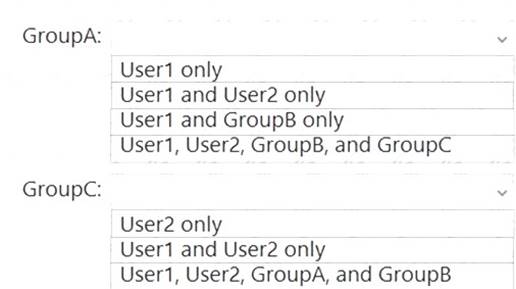
Solution:
Graphical user interface, text, application, chat or text message Description automatically generated
Does this meet the goal?
Correct Answer:
A