Which two statements are correct about EVPN-VXLAN overlay networking? (Choose two.)
Correct Answer:
BC
EVPN-VXLANis an overlay technology used in data center networks to extend Layer 2 services over a Layer 3 network.
Step-by-Step Breakdown:
BGP Control Plane:BGP (Border Gateway Protocol)is used as the control plane for EVPN-VXLAN. BGP advertises MAC addresses and IP address reachability information across the VXLAN network, enabling efficient multi-tenant Layer 2 connectivity over a Layer 3 infrastructure.
Encapsulation:VXLAN (Virtual Extensible LAN)encapsulates Layer 2 frames into Layer 3 packets. This encapsulation allows Layer 2 traffic to be transported across a Layer 3 network, effectively creating a tunnel for Ethernet frames.
Juniper Reference:
EVPN-VXLAN Configuration: Juniper supports EVPN-VXLAN with BGP as the control plane, allowing scalable Layer 2 connectivity over a routed infrastructure in modern data centers.
Exhibit: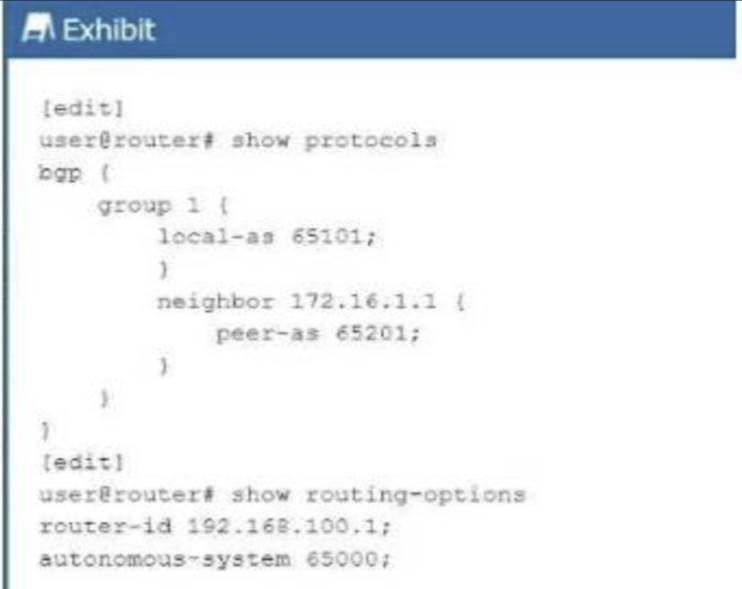
Referring to the exhibit, which statement is correct?
Correct Answer:
B
In the exhibit, BGP is configured withlocal AS 65101and a neighbor at172.16.1.1inpeer AS 65201. This setup involves two different Autonomous Systems (AS), indicating anExternal BGP (EBGP)configuration.
Step-by-Step Breakdown:  EBGP vs. IBGP:
EBGP vs. IBGP: EBGPis used between routers in different ASes. In this case, the local AS is65101and the peer AS is65201, meaning the BGP session isEBGP.
EBGPis used between routers in different ASes. In this case, the local AS is65101and the peer AS is65201, meaning the BGP session isEBGP. IBGPis used between routers within the same AS, which is not applicable here as the AS numbers are different.
IBGPis used between routers within the same AS, which is not applicable here as the AS numbers are different. BGP Group Configuration:
BGP Group Configuration: The configuration does not require a type external parameter because Junos OSautomatically recognizes the session asEBGPwhen the local and peer AS numbers are different.
The configuration does not require a type external parameter because Junos OSautomatically recognizes the session asEBGPwhen the local and peer AS numbers are different. The BGP session will operate as EBGP, and the configuration will commit successfully.
The BGP session will operate as EBGP, and the configuration will commit successfully.
Juniper Reference: BGP Configuration: In Juniper, EBGP is automatically recognized when the local and peer AS numbers differ, without needing to specify type external.
BGP Configuration: In Juniper, EBGP is automatically recognized when the local and peer AS numbers differ, without needing to specify type external.
You are creating an IP fabric underlay and want to use OSPF as your routing protocol. In this scenario, which statement is correct?
Correct Answer:
C
When creating anIP fabric underlayusingOSPFas the routing protocol, consistentinterface speedsare important to ensure optimal traffic distribution and utilization of all links.
Step-by-Step Breakdown: OSPF and Interface Speeds:OSPF calculates the cost of a link based on its bandwidth. The default cost calculation in OSPF is:
OSPF and Interface Speeds:OSPF calculates the cost of a link based on its bandwidth. The default cost calculation in OSPF is:
A black text on a white background Description automatically generated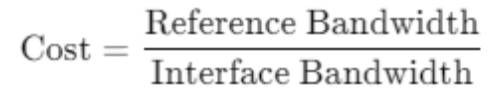
 If interface speeds vary significantly, OSPF may choose paths with lower cost (higher bandwidth), resulting in some links being underutilized.
If interface speeds vary significantly, OSPF may choose paths with lower cost (higher bandwidth), resulting in some links being underutilized. Equal Utilization:To ensure that all links are equally utilized in an IP fabric, it is recommended to maintain uniform interface speeds across the fabric. This ensures balanced load sharing across all available paths.
Equal Utilization:To ensure that all links are equally utilized in an IP fabric, it is recommended to maintain uniform interface speeds across the fabric. This ensures balanced load sharing across all available paths.
Juniper Reference: IP Fabric with OSPF: Juniper recommends consistent interface speeds to maintain even traffic distribution and optimal link utilization in IP fabric underlay designs.
IP Fabric with OSPF: Juniper recommends consistent interface speeds to maintain even traffic distribution and optimal link utilization in IP fabric underlay designs.
What information in the Ethernet header is used to populate the bridging table?
Correct Answer:
A
Thesource MAC addressin the Ethernet header is used to populate thebridging table(also called the MAC address table) on a switch. When a frame arrives at a switch, the switch examines the source MAC address and records it along with the ingress port in its MAC address table.
Step-by-Step Breakdown:
Learning Process:When an Ethernet frame arrives on a switch port, the switch looks at thesource MAC addressand adds this MAC address to the MAC table along with the port it was received on. This process is calledMAC learning.
Purpose:The switch uses this information to determine the correct port to send frames destined for that MAC address in future transmissions, thus ensuring efficient Layer 2 forwarding.
Juniper Reference:
Ethernet Switching: Juniper switches use source MAC addresses to build and maintain the MAC address table, which is essential for Layer 2 switching.
Which state in the adjacency process do OSPF routers check the MTU size?
Correct Answer:
B
In OSPF, routers exchange link-state information in different stages to establish full adjacency. TheMTU size is checked during theExchangestate.
Step-by-Step Breakdown: OSPF Adjacency Process:
OSPF Adjacency Process: OSPF routers go through multiple stages when forming an adjacency:Down,Init,2-Way,ExStart,
OSPF routers go through multiple stages when forming an adjacency:Down,Init,2-Way,ExStart,
Exchange,Loading, andFull. Exchange State:
Exchange State: During theExchangestate, OSPF routers exchangeDatabase Description (DBD)packets to describe their link-state databases. TheMTU sizeis checked at this stage to ensure both routers can successfully exchange these packets without fragmentation.
During theExchangestate, OSPF routers exchangeDatabase Description (DBD)packets to describe their link-state databases. TheMTU sizeis checked at this stage to ensure both routers can successfully exchange these packets without fragmentation. If there is anMTU mismatch, the routers may fail to proceed past the Exchange state.
If there is anMTU mismatch, the routers may fail to proceed past the Exchange state.
Juniper Reference: MTU Checking in OSPF: Junos uses the Exchange state to check for MTU mismatches, ensuring that routers can properly exchange database information without packet fragmentation issues.
MTU Checking in OSPF: Junos uses the Exchange state to check for MTU mismatches, ensuring that routers can properly exchange database information without packet fragmentation issues.