Which statement is correct about the BGP AS path when advertising routes?
Correct Answer:
D
The BGPAS (Autonomous System) pathattribute is crucial in path selection and loop prevention. Each BGP router appends itslocal AS numberto the beginning of the AS path when it advertises a route to an external BGP (eBGP) peer.
Step-by-Step Breakdown:
AS Path Attribute:The AS path is a sequence of AS numbers that a route has traversed to reach a destination. Each AS adds its number to the front of the path, allowing BGP to track the route??s history.
Why the Local AS is Added at the Beginning:When advertising a route to an eBGP neighbor, a BGP router adds its own AS number to the beginning of the AS path. This ensures that the AS path reflects the route's journey accurately from the origin to the destination, and prevents loops in BGP. If the route returns to the same AS, the router will detect its AS number in the path and reject the route, preventing routing loops.
Order of the AS Path:The order is significant because BGP uses it to select the best path. A shorter AS path is preferred, as it indicates fewer hops between the source and destination.
Juniper Reference:
AS Path Attribute: Junos devices append the local AS at the start of the AS path before advertising the route to an external peer.
How many stages are shown in the exhibit?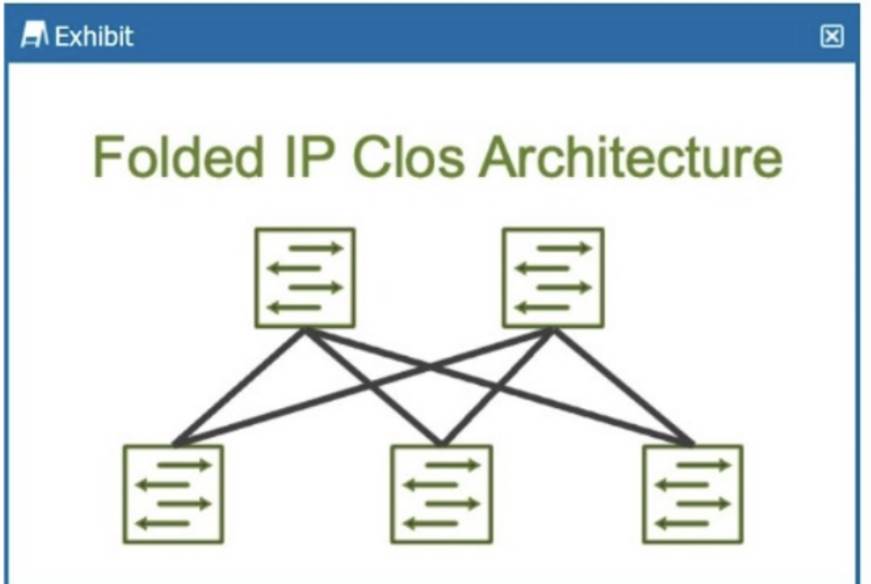
Correct Answer:
D
The exhibit shows aFolded IP Clos Architecture, which is also referred to as a3-stage Closnetwork design. This architecture typically consists of two layers of switches:
Spine Layer: The top row of switches.
Leaf Layer: The bottom row of switches.
Step-by-Step Breakdown:
Clos Architecture:A 3-stage Clos network has two types of devices: spine and leaf. In this design, each leaf switch connects to every spine switch, providing a high level of redundancy and load balancing.
Stage Explanation:
Stage 1: The first set of leaf switches.
Stage 2: The spine switches.
Stage 3: The second set of leaf switches.
TheFolded Closarchitecture shown here effectively "folds" the 3-stage design by combining the ingress and egress leaf layers into one, reducing it to two visible layers, but still maintaining the overall3-stage architecture.
Juniper Reference:
IP Clos Architecture: The 3-stage Clos design is commonly used in modern data centers for high availability, redundancy, and scalability.
Which two statements are correct about VLAN tags? (Choose two.)
Correct Answer:
AD
VLAN tagsare used in Ethernet frames to identify and differentiate traffic between multiple VLANs. They are especially important for devices like switches that handle multiple VLANs on the same physical link.
Step-by-Step Breakdown:
VLAN Tag Contents:
VLAN ID: The tag contains a 12-bit VLAN ID field that identifies the VLAN to which the frame belongs.
Priority: The tag also includes a 3-bit priority field (also known as 802.1p priority) used for QoS (Quality of Service) to prioritize traffic.
Trunk Ports and VLAN Tagging:
Trunk Portsare used to carry traffic for multiple VLANs across a single link. These interfaces insert (tag) VLAN identifiers into frames when they leave the switch and remove (untag) them when frames enter the switch.
Access Ports:VLAN tags are typically not used onaccess ports(ports that connect to end devices) since those ports are configured to be part of a single VLAN, and the traffic doesn't need VLAN tags.
Juniper Reference:
VLAN Tagging: Juniper switches support VLAN tagging and ensure that frames are tagged or untagged as they traverse trunk or access ports, respectively.
A switch receives a frame with a MAC address of FF-FF-FF-FF-FF-FF. Which action will the switch take on this frame?
Correct Answer:
A
AMAC address of FF-FF-FF-FF-FF-FFis the Ethernetbroadcast address. When a switch receives a frame with this destination MAC address, it is required to forward the frame to all interfaces except the one it was received on.
Step-by-Step Breakdown:
Broadcast Frame Handling:When a frame with the broadcast MAC address is received, the switch will flood it out of all active ports that belong to the same VLAN as the incoming frame. The broadcast frame is not sent back out of the ingress interface (the interface where the frame was originally received).
Purpose of Flooding:Broadcasting is used to ensure that the frame reaches all devices within the broadcast domain (all devices within the same VLAN), which may not have a specific entry for the MAC address in their MAC address table.
Juniper Reference:
Layer 2 Frame Forwarding: Juniper switches flood broadcast frames to all ports in the same VLAN, except the port the frame was received on.
When a MAC limiting violation occurs, the switch performs which two actions by default? (Choose two.)
Correct Answer:
CD
When aMAC limiting violationoccurs on a Juniper switch, the switch will perform the following actions by default:
Step-by-Step Breakdown: Port Disabled:When the number of MAC addresses on an interface exceeds the configured limit, the port isautomatically disabledto prevent further violations. This is a protective mechanism to prevent MAC address flooding.
Port Disabled:When the number of MAC addresses on an interface exceeds the configured limit, the port isautomatically disabledto prevent further violations. This is a protective mechanism to prevent MAC address flooding. Packet Dropped:Additionally, packets from the violating MAC address aredroppedto prevent any further communication from that address. This ensures that only valid MAC addresses are allowed to communicate through the interface.
Packet Dropped:Additionally, packets from the violating MAC address aredroppedto prevent any further communication from that address. This ensures that only valid MAC addresses are allowed to communicate through the interface. Example Configuration:
Example Configuration:
set ethernet-switching-options secure-access-port interface <interface-name> mac-limit 5 If more than five MAC addresses are learned, the port is disabled, and excess packets are dropped.
If more than five MAC addresses are learned, the port is disabled, and excess packets are dropped.
Juniper Reference: MAC Limiting: When the switch detects a MAC limiting violation, it disables the port and drops further packets from the violating MAC addresses to maintain network security.
MAC Limiting: When the switch detects a MAC limiting violation, it disables the port and drops further packets from the violating MAC addresses to maintain network security.