Which of the following response teams aims to foster cooperation and coordination in incident
prevention, to prompt rapid reaction to incidents, and to promote information sharing among members and the community at large?
Correct Answer:
C
Which of the following are examples of physical controls used to prevent unauthorized access to sensitive materials?
Correct Answer:
ABD
Which of the following statements reflect the 'Code of Ethics Preamble' in the '(ISC)2 Code of Ethics'? Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:
AB
You work as the Senior Project manager in Dotcoiss Inc. Your company has started a software project using configuration management and has completed 70% of it. You need to ensure that the network infrastructure devices and networking standards used in this project are installed in accordance with the requirements of its detailed project design documentation. Which of the following procedures will you employ to accomplish the task?
Correct Answer:
B
You are the project manager of the GHE Project. You have identified the following risks with the characteristics as shown in the following figure: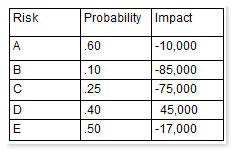
How much capital should the project set aside for the risk contingency reserve?
Correct Answer:
D