- (Topic 4)
You work as a Network Administrator for Tech Perfect Inc. You have a laptop running Windows Vista Ultimate. You want to configure Windows Defender on your laptop so that it does not take any action automatically whenever it scans malicious software. Rather, it should recommend the action and wait for your approval for taking any action. Which of the following actions will you take to accomplish the task?
Correct Answer:
D
According to the question, you want to prevent Windows Defender from taking any action automatically during the scanning of your laptop. In order to accomplish this, you will have to clear the Apply default actions to items detected during a scan check box in Defender Options.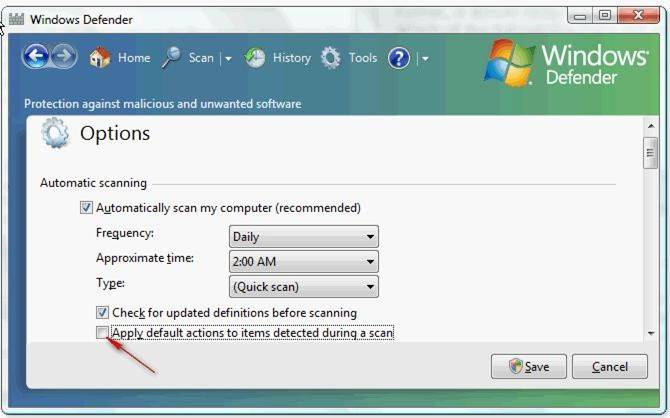
If you clear the Apply default actions to items detected during a scan check box, it will result in Windows Defender only recommending an action to take for detected malicious software.
- (Topic 1)
You work as a Network Administrator for XYZ CORP. The company has a Linux-based network. You need to configure a firewall for the company. The firewall should be able to keep track of the state of network connections traveling across the network. Which of the following types of firewalls will you configure to accomplish the task?
Correct Answer:
D
A stateful firewall is a firewall that keeps track of the state of network connections (such as TCP streams, UDP communication) traveling across it. The firewall is programmed to distinguish legitimate packets for different types of connections. Only packets matching a known connection state will be allowed by the firewall; others will be rejected. Answer B is incorrect. A host-based application firewall can monitor any application input, output, and/or system service calls made from, to, or by an application. This is done by examining information passed through system calls instead of, or in addition to, a network stack. A host-based application firewall can only provide protection to the applications running on the same host. An example of a host-based application firewall that controls system service calls by an application is AppArmor or the Mac OS X application firewall. Host-based application firewalls may also provide network-based application firewalling. Answer A is incorrect. A network-based application layer firewall, also known as a proxy-based or reverse-proxy firewall, is a computer networking firewall that operates at the application layer of a protocol stack. Application firewalls specific to a particular kind of network traffic may be titled with the service name, such as a Web application firewall. They may be implemented through software running on a host or a stand-alone piece of network hardware. Often, it is a host using various forms of proxy servers to proxy traffic before passing it on to the client or server. Because it acts on the application layer, it may inspect the contents of the traffic, blocking specified content, such as certain websites, viruses, and attempts to exploit known logical flaws in client software. Answer C is incorrect. An application firewall is a form of firewall that controls input, output, and/or access from, to, or by an application or service. It operates by monitoring and potentially blocking the input, output, or system service calls that do not meet the configured policy of the firewall. The application firewall is typically built to monitor one or more specific applications or services (such as a web or database service), unlike a stateful network firewall, which can provide some access controls for nearly any kind of network traffic. There are two primary categories of application firewalls: Network-based application firewalls Host-based application firewalls
- (Topic 4)
Which TCP and UDP ports can be used to start a NULL session attack in NT and 2000 operating systems?
Correct Answer:
C
A null session is an anonymous connection to a freely accessible network share called IPC$ on Windows-based servers. It allows immediate read and write access with Windows NT/2000 and read-access with Windows XP and 2003. The command to be inserted at the DOS-prompt is as follows: net use \\IP address_or_host name\ipc$ "" "/user:" net use Port numbers 139 TCP and 445 UDP can be used to start a NULL session attack.
- (Topic 1)
Which of the following tools is used to make fake authentication certificates?
Correct Answer:
C
WinSSLMiM is an HTTPS Man in the Middle attacking tool. It includes FakeCert, a tool used to make fake certificates. It can be used to exploit the Certificate Chain vulnerability in Internet Explorer. The tool works under Windows 9x/2000. For example, Generate fake certificate: fc -s www.we-are-secure.com -f fakeCert.crt Launch WinSSLMiM: wsm -f fakeCert.crt Answer D is incorrect. Brutus is a password cracking tool that performs both dictionary and brute force attacks in which passwords are randomly generated from given characters. Brute forcing can be performed on the following authentications: HTTP (Basic Authentication) HTTP (HTML Form/CGI) POP3 (Post Office Protocol v3) FTP (File Transfer Protocol) SMB (Server Message Block) Telnet Answer A is incorrect. Obiwan is a Web password cracking tool that is used to perform brute force and hybrid attacks. It is effective against HTTP connections for Web servers that allow unlimited failed login attempts by the user. Obiwan uses wordlists as well as alphanumeric characters as possible passwords. Answer B is incorrect. Netcat is a freely available networking utility that reads and writes data across network connections by using the TCP/IP protocol. Netcat has the following features: It provides outbound and inbound connections for TCP and UDP ports. It provides special tunneling such as UDP to TCP, with the possibility of specifying all network parameters. It is a good port scanner. It contains advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of transmitted and received data. It is an optional RFC854 telnet code parser and responder.
- (Topic 1)
You have to move the whole directory /foo to /bar. Which of the following commands will you use to accomplish the task?
Correct Answer:
C
You will use the mv /foo /bar command to move the whole directory /foo to /bar. The mv command moves files and directories from one directory to another or renames a file or directory. mv must always be given at least two arguments. The first argument is given as a source file. The second argument is interpreted as the destination. If destination is an existing directory, the source file is moved to that directory with the same name as the source. If the destination is any other directory, the source file is moved and/or renamed to that destination name. Syntax : mv [options] source destination Some important options used with mv command are as follows: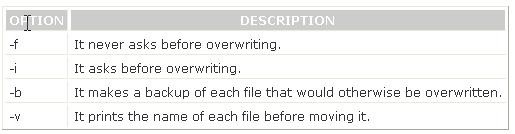
Answer A is incorrect. The mv /bar /foo command will move the whole /bar directory to the /foo directory. Answer B, D are incorrect. These are not valid Linux commands.