- (Topic 2)
You work as a Network Administrator for XYZ CORP. The company has a Windows-based network. You want to use multiple security countermeasures to protect the integrity of the information assets of the company. To accomplish the task, you need to create a complex and multi-layered defense system. Which of the following components can be used as a layer that constitutes 'Defense in depth'? (Choose three)
Correct Answer:
BCD
The components of Defense in depth include antivirus software, firewalls, anti-spyware programs, hierarchical passwords, intrusion detection, and biometric verification. In addition to electronic countermeasures, physical protection of business sites along with comprehensive and ongoing personnel training enhances the security of vital data against compromise, theft, or destruction. Answer A is incorrect. A backdoor is any program that allows a hacker to connect to a computer without going through the normal authentication process. The main advantage of this type of attack is that the network traffic moves from inside a network to the hacker's computer. The traffic moving from inside a network to the outside world is typically the least restrictive, as companies are more concerned about what comes into a network, rather than what leaves it. It, therefore, becomes hard to detect backdoors.
- (Topic 3)
You work as a Network Administrator for Net World International. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. There are ten Sales Managers in the company. The company has recently provided laptops to all its Sales Managers. All the laptops run Windows XP Professional. These laptops will be connected to the company's network through wireless connections. The company's management wants to implement Shared Key authentication for these laptops. When you try to configure the network interface card of one of the laptops for Shared Key authentication, you find no such option. What will you do to enable Shared Key authentication?
Correct Answer:
B
Shared Key authentication requires the use of the Wired Equivalent Privacy (WEP) algorithm. If the WEP is not implemented, then the option for Shared Key authentication is not available. In order to accomplish the task, you will have to enable the WEP on all the laptops.
- (Topic 1)
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
Correct Answer:
C
In Unix, the dumpe2fs command dumps the filesystem superblock and blocks the group information. Answer B is incorrect. In Unix, the dump command is used to back up an ext2 filesystem. Answer A is incorrect. The e2fsck command is used to check the second extended file system (E2FS) of a Linux computer. Syntax: e2fsck [options]
<device> Where, <device> is the file name of a mounted storage device (for example,
/dev/hda1). Several options are used with the e2fsck command. Following is a list of some important options: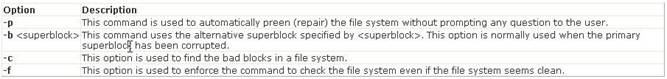
Answer D is incorrect. In Unix, the e2label command is used to change the label of an ext2 filesystem.
- (Topic 2)
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Correct Answer:
BCD
An attacker can use Host, Dig, and NSLookup to perform a DNS zone transfer. Answer A is incorrect. DSniff is a sniffer that can be used to record network traffic. Dsniff is a set of tools that are used for sniffing passwords, e-mail, and HTTP traffic. Some of the tools of Dsniff include dsniff, arpredirect, macof, tcpkill, tcpnice, filesnarf, and mailsnarf. Dsniff is highly effective for sniffing both switched and shared networks. It uses the arpredirect and macof tools for switching across switched networks. It can also be used to capture authentication information for FTP, telnet, SMTP, HTTP, POP, NNTP, IMAP, etc.
- (Topic 4)
What will happen if you write the following parameters in the web.xml file?
Correct Answer:
B
The <session-timeout> element of the deployment descriptor sets the session timeout. If the time specified for timeout is zero or negative, the session will never timeout.