- (Topic 2)
In a network, a data packet is received by a router for transmitting it to another network. In order to make decisions on where the data packet should be forwarded, the router checks with its routing table. Which of the following lists does a router check in a routing table?
Correct Answer:
AD
A Routing table stores the actual routes to all destinations; the routing table is populated from the topology table with every destination network that has its successor and optionally feasible successor identified (if unequal-cost load-balancing is enabled using the variance command). The successors and feasible successors serve as the next hop routers for these destinations. Unlike most other distance vector protocols, EIGRP does not rely on periodic route dumps in order to maintain its topology table. Routing information is exchanged only upon the establishment of new neighbor adjacencies, after which only changes are sent. Answer C is incorrect. A routing table does not contain any list of protocols. Answer B is incorrect. A routing table does not contain any list of packets.
- (Topic 4)
You work as a Network Analyst for XYZ CORP. The company has a Unix-based network. You want to view the directories in alphabetical order. Which of the following Unix commands will you use to accomplish the task?
Correct Answer:
D
In Unix, the ls command is used to view the directories in alphabetical order. Answer A is incorrect. In Unix, the cat command in Unix is used to create or display short files. Answer B is incorrect. In Unix, the chmod command is used to change permissions. Answer C is incorrect. In Unix, the cp command is used for copying files.
- (Topic 3)
Data access auditing is a surveillance mechanism that watches over access to all sensitive information contained within the database. What are the questions addressed in a perfect data access auditing solution?
Correct Answer:
ABD
The perfect data access auditing solution would address the following six questions: 1.Who accessed the data? 2.When was the data accessed? 3.Which computer program or client software was used to access the data? 4.From what location on the network was the data accessed? 5.What was the SQL query that accessed the data? 6.Was access to the data successfully done; and if so, how many rows of data were retrieved? Answer C is incorrect. In the perfect data access auditing solution, it cannot be determined for whom the data is being accessed. Only the person accessing the data can be identified.
- (Topic 2)
You want to change the number of characters displaying on the screen while reading a txt file. However, you do not want to change the format of the txt file. Which of the following commands can be used to view (but not modify) the contents of the text file on the terminal screen at a time?
Correct Answer:
D
The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,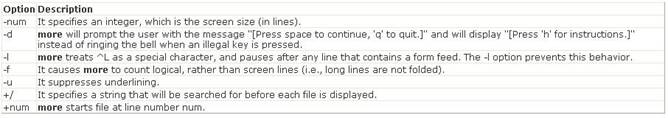
Answer A is incorrect. The concatenate (cat) command is used to display or print the contents of a file. Syntax: cat filename For example, the following command will display the contents of the /var/log/dmesg file: cat /var/log/dmesg Note: The more command is used in conjunction with the cat command to prevent scrolling of the screen while displaying the contents of a file. Answer C is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,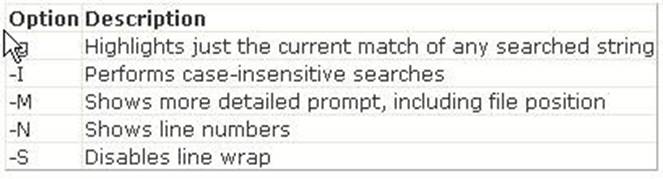
Answer B is incorrect. The tail command is used to display the last few lines of a text file or piped data.
- (Topic 2)
Which of the following applications work as mass-emailing worms? (Choose two)
Correct Answer:
BC
The Nimda and I LOVE YOU viruses work as mass-emailing worms.