- (Topic 1)
You work as a Network Administrator for Blue Well Inc. The company has a TCP/IP-based routed network. Two segments have been configured on the network as shown below: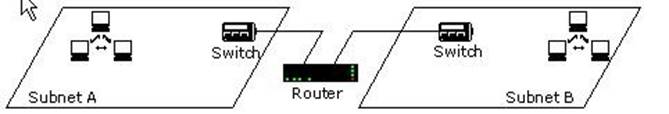
One day, the switch in Subnet B fails. What will happen?
Correct Answer:
AD
According to the question, the network is a routed network where two segments have been divided and each segment has a switch. These switches are connected to a common router. All workstations in a segment are connected to their respective subnet's switches. Failure of the switch in Subnet B will make all workstations connected to it offline. Moreover, communication between the two subnets will be affected, as there will be no link to connect to Subnet B.
- (Topic 4)
Which of the following NFS mount options specifies whether a program using a file via an NFS connection should stop and wait for the server to come back online, if the host serving the exported file system is unavailable, or if it should report an error?
Correct Answer:
B
The hard or soft NFS mount options are used to specify whether a program using a file via an NFS connection should stop and wait (hard) for the server to come back online, if the host serving the exported file system is unavailable, or if it should report an error. Answer A is incorrect. The intr NFS mount option allows NFS requests to be interrupted if the server goes down or cannot be reached. Answer C is incorrect. The nfsvers=2 or nfsvers=3 NFS mount options are used to specify which version of the NFS protocol to use. Answer D is incorrect. The fsid=num NFS mount option forces the file handle and file attributes settings on the wire to be num.
- (Topic 3)
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP based switched network. A root bridge has been elected in the switched network. You have installed a new switch with a lower bridge ID than the existing root bridge. What will happen?
Correct Answer:
A
The new switch starts advertising itself as the root bridge. It acts as it is the only bridge on the network. It has a lower Bridge ID than the existing root, so it is elected as the root bridge after the BPDUs converge and when all switches know about the new switch that it is the better choice. Answer B, C, D are incorrect. All these are not valid options, according to the given scenario.
- (Topic 2)
You want to record auditing information in the SYS.AUD$ table, and also want to record SQL bind variables as well as the SQL text in the audit trail. Which of the following statements will accomplish this task?
Correct Answer:
CD
The initialization parameter AUDIT_TRAIL is used to specify the kind of auditing that needs to be performed, as well as the destination where it will be performed. There are three basic values for auditing that are DB, OS, and XML. Specifying DB sends all audit rows to the table SYS.AUD$, OS sends the audit rows to an operating system file, and XML sends the audit rows to an operating system file in the XML format. The location for external audit rows is specified by the AUDIT_FILE_DEST parameter. By adding the EXTENDED parameter for either DB or XML auditing, all SQL bind variables and the text of all SQL commands are included in the audit row. EXTENDED cannot be specified for OS auditing. In addition, NONE can be specified as the value for AUDIT_TRAIL, which will disable all auditing. Answer B is incorrect. DB, EXTENDED in single quotes cannot be specified when setting the AUDIT_TRAIL parameter. Answer E is incorrect. AUDIT_TRAIL must be set to specify the type of auditing. AUDIT_FILE_DEST is used to specify the operating system location for either OS or XML auditing. Answer A is incorrect. DB and XML auditing cannot be specified at the same time and the database must be restarted for the auditing change to go into effect.
- (Topic 2)
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
Correct Answer:
AB
Following are the limitations of cross site request forgeries to be successful:
* 1. The attacker must target either a site that doesn't check the Referer header (which is common) or a victim with a browser or plugin bug that allows Referer spoofing (which is rare).
* 2. The attacker must find a form submission at the target site that does something useful to the attacker (e.g., transfers money, or changes the victim's e-mail address or password).
* 3. The attacker must determine the right values for all the form inputs: if any of them are required to be secret authentication values or IDs that the attacker can't guess, the attack will fail.
* 4. The attacker must lure the victim to a Web page with malicious code while the victim is logged in to the target site. Since, the attacker can't see what the target Web site sends back to the victim in response to the forged requests, unless he exploits a cross- site scripting or other bug at the target Web site.
Similarly, the attacker can only "click" any links or submit any forms that come up after the initial forged request, if the subsequent links or forms are similarly predictable. (Multiple "clicks" can be simulated by including multiple images on a page, or by using JavaScript to introduce a delay between clicks). from cross site request forgeries (CSRF) by applying the following countermeasures available: Requiring authentication in GET and POST parameters, not only cookies. Checking the HTTP Referer header. Ensuring there's no crossdomain.xml file granting unintended access to Flash movies. Limiting the lifetime of authentication cookies. Requiring a secret, user-specific token in all form submissions prevents CSRF; the attacker's site can't put the right token in its submissions. Individual Web users can do relatively little to prevent cross-site request forgery. Logging out of sites and avoiding their "remember me" features can mitigate CSRF risk; not displaying external images or not clicking links in "spam" or unreliable e-mails may also help.