- (Topic 2)
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the username, real name, home directory, encrypted password, and other information about a user. Which of the following Unix configuration files can you use to accomplish the task?
Correct Answer:
A
In Unix, the /etc/passwd file contains username, real name, home directory,
encrypted password, and other information about a user. Answer C is incorrect. In Unix, the /etc/hosts file lists the hosts for name lookup use that are locally required. Answer D is incorrect. In Unix, the /etc/inittab file is the configuration file for init. It controls startup run levels and determines scripts to start with. Answer B is incorrect. In Unix, the /etc/printcap file is the configuration file for printers.
- (Topic 3)
Which of the following is an attempt to give false information or to deny that a real event or transaction should have occurred?
Correct Answer:
B
A repudiation attack is an attempt to give false information or to deny that a real event or transaction should have occurred. Answer A is incorrect. In a distributed denial of service (DDOS) attack, an attacker uses multiple computers throughout the network that has been previously infected. Such computers act as zombies and work together to send out bogus messages, thereby increasing the amount of phony traffic. The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. TFN, TRIN00, etc. are tools used for a DDoS attack. Answer C is incorrect. A replay attack is a type of attack in which attackers capture packets containing passwords or digital signatures whenever packets pass between two hosts on a network. In an attempt to obtain an authenticated connection, the attackers then resend the captured packet to the system. In this type of attack, the attacker does not know the actual password, but can simply replay
the captured packet. Answer D is incorrect. Dictionary attack is a type of password guessing attack. This type of attack uses a dictionary of common words to find out the password of a user. It can also use common words in either upper or lower case to find a password. There are many programs available on the Internet to automate and execute dictionary attacks.
- (Topic 1)
John visits an online shop that stores the IDs and prices of the items to buy in a cookie. After selecting the items that he wants to buy, the attacker changes the price of the item to
* 1. Original cookie values: ItemID1=2 ItemPrice1=900 ItemID2=1 ItemPrice2=200 Modified cookie values: ItemID1=2 ItemPrice1=1 ItemID2=1 ItemPrice2=1 Now, he clicks the Buy button, and the prices are sent to the server that calculates the total price. Which of the following hacking techniques is John performing?
Correct Answer:
C
John is performing cookie poisoning. In cookie poisoning, an attacker modifies the value of cookies before sending them back to the server. On modifying the cookie values, an attacker can log in to any other user account and can perform identity theft. The following figure explains how cookie poisoning occurs: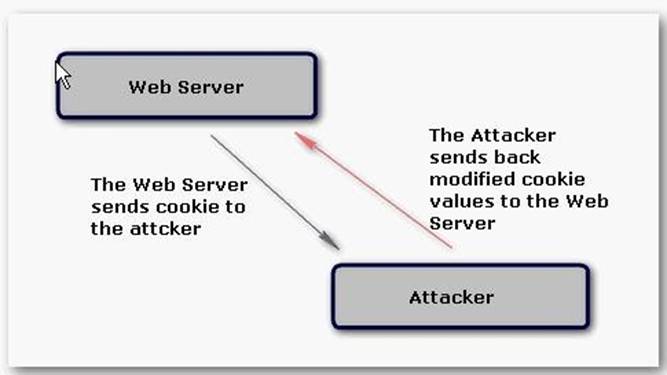
For example: The attacker visits an online shop that stores the IDs and prices of the items to buy in a cookie. After selecting the items that he wants to buy, the attacker changes the price of the item to 1. Original cookie values: ItemID1= 2 ItemPrice1=900 ItemID2=1 ItemPrice2=200 Modified cookie values: ItemID1= 2 ItemPrice1=1 ItemID2=1 ItemPrice2=1 Now, the attacker clicks the Buy button and the prices are sent to the server that calculates the total price. Another use of a Cookie Poisoning attack is to pretend to be another user after changing the username in the cookie values: Original cookie values: LoggedIn= True Username = Mark Modified cookie values: LoggedIn= True Username = Admin Now, after modifying the cookie values, the attacker can do the admin login.
Answer A is incorrect. A cross site scripting attack is one in which an attacker enters malicious data into a Website. For example, the attacker posts a message that contains malicious code to any newsgroup site. When another user views this message, the browser interprets this code and executes it and, as a result, the attacker is able to take control of the user's system. Cross site scripting attacks require the execution of client-side languages such as JavaScript, Java, VBScript, ActiveX, Flash, etc. within a user's Web environment. With the help of a cross site scripting attack, the attacker can perform cookie stealing, sessions hijacking, etc.
- (Topic 4)
You work as a Network Architect for Tech Perfect Inc. The company has a TCP/IP based Enterprise network. The company uses Cisco IOS technologies in the Enterprise network. You have enabled system message logging (syslog) service on all the routers that are currently working in the network. The syslog service provides all the reports, and important error and notification messages. You want to store all the reports and messages. Choose the locations where you can store all of these.
Correct Answer:
BCDE
According to the scenario, you have enabled system message logging (syslog) service on all the routers that are currently working in the network. If you want to store all the repots, important error and notification messages sent by the routers, you can store all of these in the buffer, console, syslog server, and tty lines. You can use buffer, if you want to store syslog messages for later analysis of the network. Buffer is the memory of the router. The syslog messages that you have stored in the buffer are later available for the network analysis until the router is rebooted. You can use console port of the routers to send syslog messages to the attached terminal. You can also use vty and tty lines to send syslog messages to the remote terminal. However, the messages send through the console, vty, and tty lines are not later available for network analysis. You can use syslog server to store all the reports, and important error and notification messages. It is the best option to store all these because it is easy to configure a syslog server and you can store a large volume of logs. Note: If you have configured to run an SNMP agent, the routers send all the reports, and important error and messages in the form of SNMP traps to an SNMP server. Using this you can store the reports and messages for a long period of time. Answer A is incorrect. You cannot store syslog messages in the auxiliary line.
- (Topic 3)
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
Correct Answer:
B
According to the scenario, John is performing the Steganography technique for sending malicious data. Steganography is an art and science of hiding information by embedding harmful messages within other seemingly harmless messages. It works by replacing bits of unused data, such as graphics, sound, text, and HTML, with bits of invisible information in regular computer files. This hidden information can be in the form of plain text, cipher text, or even in the form of images. Answer A is incorrect. Web ripping is
a technique in which the attacker copies the whole structure of a Web site to the local disk and obtains all files of the Web site. Web ripping helps an attacker to trace the loopholes of the Web site. Answer D is incorrect. Social engineering is the art of convincing people and making them disclose useful information such as account names and passwords. This information is further exploited by hackers to gain access to a user's computer or network. This method involves mental ability of the people to trick someone rather than their technical skills. A user should always distrust people who ask him for his account name or password, computer name, IP address, employee ID, or other information that can be misused. Answer C is incorrect. John is not performing email spoofing. In email spoofing, an attacker sends emails after writing another person's mailing address in the from field of the email id.