- (Topic 2)
You want to repeat the last command you entered in the bash shell. Which of the following commands will you use?
Correct Answer:
C
The history !! command shows the previously entered command in the bash shell. In the bash shell, the history command is used to view the recently executed commands. History is on by default. A user can turn off history using the command set +o history and turn it on using set -o history. An environment variable HISTSIZE is used to inform bash about how many history lines should be kept. The following commands are frequently used to view
and manipulate history: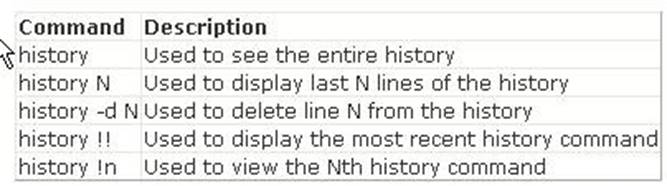
Answer B is incorrect. The history !# command shows the entire command line typed. Answer D is incorrect. The history !n command shows the nth command typed. Since n is equal to 1 in this command, the first command will be shown. Answer A is incorrect. It is not a valid command.
- (Topic 3)
Which of the following tags will create two vertical frames, as given in the image below, where the left frame is half as wide as the right one?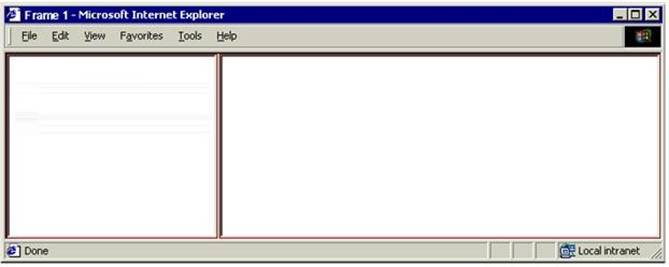
Correct Answer:
E
<FRAMESET> tag specifies a frameset used to organize multiple frames and nested framesets in an HTML document. It defines the location, size, and orientation of frames. An HTML document can either contain a
<FRAMESET> tag or a <BODY> tag. The COLS attribute of the
<FRAMESET> tag defines the width of the vertical frames. The ROWS attribute defines the height of the horizontal frames. The code in answer option E will create two identical frames. The left frame will be half as wide as the right frame because of the relative size attributes given in the <FRAMESET> tag, i.e.,
<FRAMESET COLS = "*, 2*">.
- (Topic 1)
Which of the following statements about a screened host is true?
Correct Answer:
C
A screened host provides added security by using Internet access to deny or permit certain traffic from the Bastion Host. Answer D is incorrect. A network interface card provides a physical connection between computers within a network.
Answer B is incorrect. Demilitarized zone (DMZ) or perimeter network is a small network that lies in between the Internet and a private network. It is the boundary between the Internet and an internal network, usually a combination of firewalls and bastion hosts that are gateways between inside networks and outside networks. DMZ provides a large enterprise network or corporate network the ability to use the Internet while still maintaining its security. Answer A is incorrect. A proxy server facilitates a more efficient use of the Internet connection bandwidth and hides the real IP addresses of computers located behind the proxy.
- (Topic 2)
Which of the following text editing tools can be used to edit text files without having to open them?
Correct Answer:
B
The Unix utility sed (stream editor) is a text editing tool that can be used to edit text files without having to open them. This utility parses text files and implements a programming language which can apply textual transformations to such files. It reads input files line by line (sequentially), applying the operation which has been specified via the command line (or a sed script), and then outputs the line. Answer D is incorrect. The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,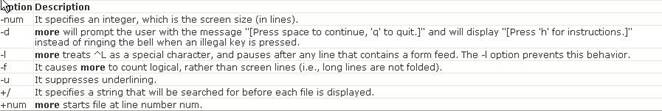
Answer A is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,
Answer C is incorrect. The vi editor is an interactive, cryptic, and screen-based text editor used to create and edit a file. It operates in either Input mode or Command mode. In Input mode, the vi editor accepts a keystroke as text and displays it on the screen, whereas in Command mode, it interprets keystrokes as commands. As the vi editor is case sensitive, it interprets the same character or characters as different commands, depending upon whether the user enters a lowercase or uppercase character. When a user starts a new session with vi, he must put the editor in Input mode by pressing the "I" key. If he is not able to see the entered text on the vi editor's screen, it means that he has not put the editor in Insert mode. The user must change the editor to Input mode before entering any text so that he can see the text he has entered.
- (Topic 3)
Which of the following statements is true about the Digest Authentication scheme?
Correct Answer:
A
The Digest Authentication scheme is a replacement of the Basic Authentication scheme. This authentication scheme is based on the challenge response model. In Digest authentication, the password is never sent across the network in clear text format but is always transmitted as an MD5 digest of the user's password. In this way, the password cannot be determined with the help of a sniffer.
How does it work? In this authentication scheme, an optional header allows the server to specify the algorithm used to create the checksum or digest (by default, the MD5 algorithm). The Digest Authentication scheme provides the challenge using a randomly chosen value. This randomly chosen value is a server-specified data string which may be uniquely generated each time a 401 response is made. A valid response contains a checksum (by default, the MD5 checksum) of the username, the password, the given random value, the HTTP method, and the requested URL. In this way, the password is never sent in clear text format. Drawback: Although the password is not sent in clear text format, an attacker can gain access with the help of the digested password, since the digested password is really all the information needed to access the web site. Answer B, C, D are incorrect. These statements are true about the Basic Authentication scheme.