When an IIS filename extension is mapped, what does this mean?
Correct Answer:
B
Included below is the output from a resource kit utility run against local host.
Which command could have produced this output? 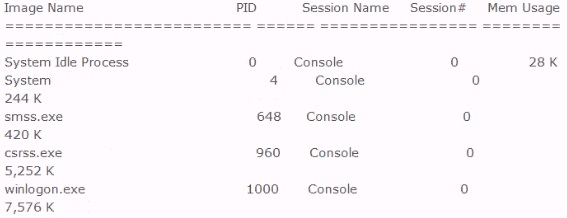
Correct Answer:
D
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. He is working as a root user on the Linux operating system. He wants to delete his private.txt file from his operating system. He knows that the deleted file can be recovered easily. Hence, he wants to delete the file securely. He wants to hide the shredding, and so he desires to add a final overwrite of the file private.txt with zero. Which of the following commands will John use to accomplish his task?
Correct Answer:
C
Which of the following applications cannot proactively detect anomalies related to a computer?
Correct Answer:
B
Which of the following statements about Hypertext Transfer Protocol Secure (HTTPS) are true? Each correct answer represents a complete solution. Choose two.
Correct Answer:
AB