- (Topic 3)
One of the sales people in your company complains that sometimes he gets a lot of unsolicited messages on his PDA. After asking a few questions, you determine that the issue only occurs in crowded areas like airports. What is the most likely problem?
Correct Answer:
B
- (Topic 3)
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a multimedia enabled mobile phone, which is suspected to be used in a cyber crime. Adam uses a tool, with the help of which he can recover deleted text messages, photos, and call logs of the mobile phone. Which of the following tools is Adam using?
Correct Answer:
C
- (Topic 1)
Analyze the screenshot below. What type of vulnerability is being attacked? 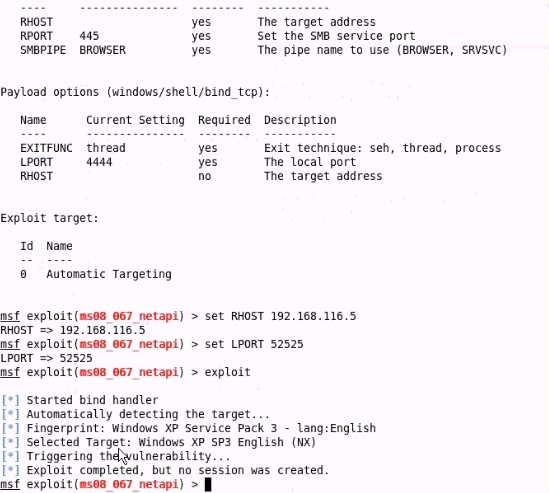
Correct Answer:
B
- (Topic 2)
Which of the following tools can be used as a Linux vulnerability scanner that is capable of identifying operating systems and network services?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:
AD
- (Topic 4)
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:
BD