- (Topic 1)
Which of the following is a method of gathering user names from a Linux system?
Correct Answer:
C
Reference:
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/pdf/Security_Guide/Red_Hat_Enterprise_Linux-6-Security_Guide-en-US.pdf
- (Topic 2)
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash? 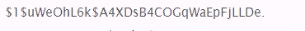
Correct Answer:
C
- (Topic 2)
Which of the following tasks can be performed by using netcat utility? Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:
ABC
- (Topic 1)
What command will correctly reformat the Unix passwordcopy and shadowcopy Tiles for input to John The Ripper?
Correct Answer:
C
Reference:
https://books.google.co.in/books?id=SC-tAwAAQBAJ&pg=PA286&lpg=PA286&dq=/Unshadow+shadow+copy+passwd+copy+%3Ej ohn+file&source=bl&ots=OnZK9atlc1&sig=co7EM5EHye96vO74W3wZxky3sXU&hl=en&sa =X&ei=FBuoVPLHDc-cugSDxYGYBA&ved=0CCwQ6AEwAg#v=onepage&q=%2FUnshadow%20shadow%20cop y%20passwd%20copy%20%3Ejohn%20file&f=false
- (Topic 1)
Why is it important to have a cheat sheet reference of database system tables when performing SQL Injection?
Correct Answer:
D
Reference: http://www.rackspace.com/knowledge_center/article/sql-injection-in-mysql