- (Topic 3)
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com network. Now, when you have finished your penetration testing, you find that the weare- secure.com server is highly vulnerable to SNMP enumeration. You advise the we-are-secure Inc. to turn off SNMP; however, this is not possible as the company is using various SNMP services on its remote nodes. What other step can you suggest to remove SNMP vulnerability?
Each correct answer represents a complete solution. Choose two.
Correct Answer:
BC
- (Topic 3)
You are using the dsniff tool to intercept communications between two entities and establish credentials with both sides of the connections. These entities do not notice that you were retrieving the information between these two. Which of the following attacks are you performing?
Correct Answer:
A
- (Topic 1)
Analyze the screenshot below. What event is depicted? 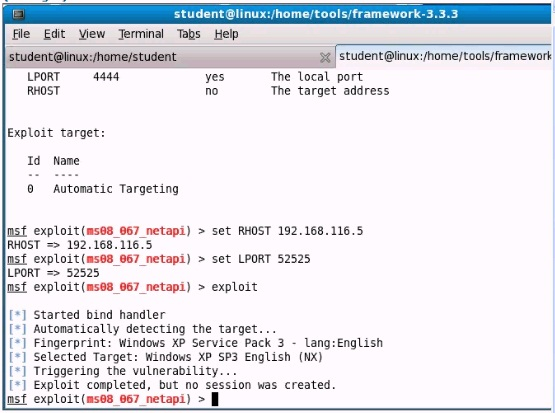
Correct Answer:
D
- (Topic 3)
When you conduct the XMAS scanning using Nmap, you find that most of the ports scanned do not give a response. What can be the state of these ports?
Correct Answer:
B
- (Topic 3)
You work as a Network Administrator for Tech Perfect Inc. The company requires a secure wireless network. To provide security, you are configuring ISA Server 2006 as a firewall. While configuring ISA Server 2006, which of the following is NOT necessary?
Correct Answer:
A