Which of the following is a type of computer security vulnerability typically found in Web applications that allow code injection by malicious Web users into the Web pages viewed by other users?
Correct Answer:
C
Which of the following tools combines two programs, and also encrypts the resulting package in an attempt to foil antivirus programs?
Correct Answer:
A
Which of the following ensures that a party to a dispute cannot deny the authenticity of their signature on a document or the sending of a message that they originated?
Correct Answer:
C
Choose and reorder the steps of an incident handling process in their correct order.
Solution: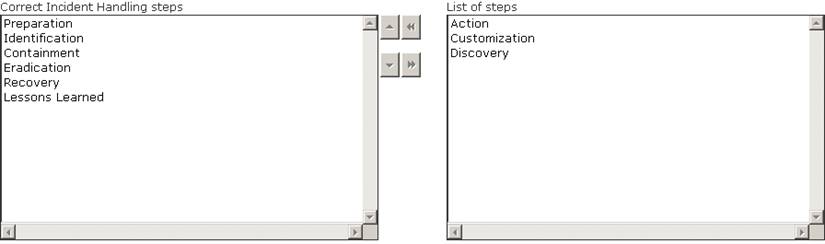
Does this meet the goal?
Correct Answer:
A
Adam, a malicious hacker purposely sends fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65,536 bytes. On the basis of above information, which of the following types of attack is Adam attempting to perform?
Correct Answer:
B