You enter the following URL on your Web browser:
http://www.we-are-secure.com/scripts/..%co%af../..%co%
af../windows/system32/cmd.exe?/c+dir+c:
What kind of attack are you performing?
Correct Answer:
A
Which of the following rootkits patches, hooks, or replaces system calls with versions that hide information about the attacker?
Correct Answer:
A
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre -test phases of the attack to test the security of weare-secure.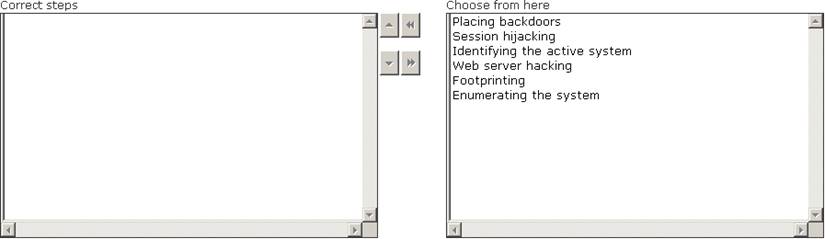
Solution: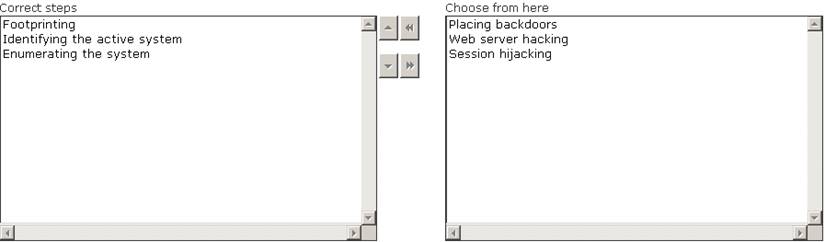
Does this meet the goal?
Correct Answer:
A
CORRECT TEXT
Fill in the blank with the appropriate term.
______ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.
Correct Answer:
Ingressfiltering
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:
AB