Which of the following Trojans is used by attackers to modify the Web browser settings?
Correct Answer:
A
Which of the following methods can be used to detect session hijacking attack?
Correct Answer:
D
Which of the following rootkits is able to load the original operating system as a virtual machine, thereby enabling it to intercept all hardware calls made by the original operating system?
Correct Answer:
C
Adam works as a Security Administrator for the Umbrella Inc. A project has been assigned to him to strengthen the security policies of the company, including its password policies. However, due to some old applications, Adam is only able to enforce a password group policy in Active Directory with a minimum of 10 characters. He informed the employees of the company, that the new password policy requires that everyone must have complex passwords with at least 14 characters. Adam wants to ensure that everyone is using complex passwords that meet the new security policy requirements. He logged on to one of the network's domain controllers and runs the following command: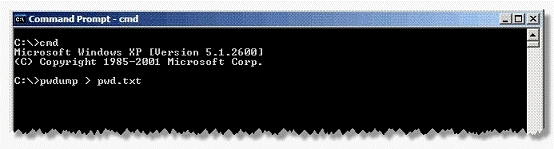
Which of the following actions will this command take?
Correct Answer:
A
Which of the following HTTP requests is the SQL injection attack?
Correct Answer:
C