Adam works as a Network Administrator for CertLeader Inc. He wants to prevent the network from
DOS attacks. Which of the following is most useful against DOS attacks?
Correct Answer:
C
Which of the following snort keywords is used to match a defined payload value?
Correct Answer:
A
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover. Which of the following Steganography methods is Victor using to accomplish the task?
Correct Answer:
A
Which of the following protocols is used to translate IP addresses to Ethernet addresses?
Correct Answer:
C
Which of the following utilities produces the output shown in the image below?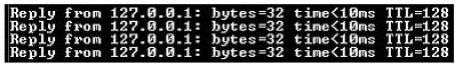
Correct Answer:
B