Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Correct Answer:
BC
For SSL VPN to function correctly between two FortiGate devices, the following settings are required: B. The server FortiGate requires a CA certificate to verify the client FortiGate certificate: The server FortiGate must have a Certificate Authority (CA) certificate installed to authenticate and verify the certificate presented by the client FortiGate device.
B. The server FortiGate requires a CA certificate to verify the client FortiGate certificate: The server FortiGate must have a Certificate Authority (CA) certificate installed to authenticate and verify the certificate presented by the client FortiGate device. C. The client FortiGate requires a client certificate signed by the CA on the server FortiGate: The client FortiGate must have a client certificate that is signed by the same CA that the server FortiGate uses for verification. This ensures a secure SSL VPN connection between the two devices.
C. The client FortiGate requires a client certificate signed by the CA on the server FortiGate: The client FortiGate must have a client certificate that is signed by the same CA that the server FortiGate uses for verification. This ensures a secure SSL VPN connection between the two devices.
The other options are not directly necessary for establishing SSL VPN: A. The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN: This is incorrect as SSL VPN does not require a specific tunnel interface type; it typically uses an SSL VPN client profile.
A. The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN: This is incorrect as SSL VPN does not require a specific tunnel interface type; it typically uses an SSL VPN client profile. D. The client FortiGate requires a manually added route to remote subnets: While routing may be necessary, it is not specifically required for the SSL VPN functionality between two FortiGates.
D. The client FortiGate requires a manually added route to remote subnets: While routing may be necessary, it is not specifically required for the SSL VPN functionality between two FortiGates.
References FortiOS 7.4.1 Administration Guide - Configuring SSL VPN, page 1203.
FortiOS 7.4.1 Administration Guide - Configuring SSL VPN, page 1203.  FortiOS 7.4.1 Administration Guide - SSL VPN Authentication, page 1210.
FortiOS 7.4.1 Administration Guide - SSL VPN Authentication, page 1210.
Refer to the exhibit.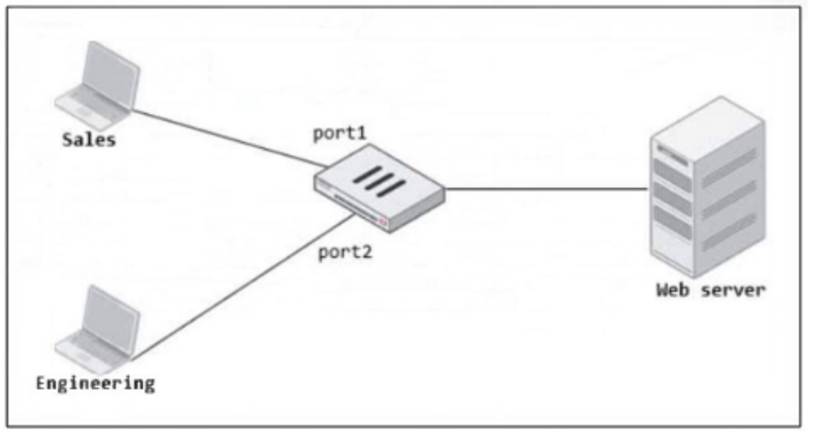
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
Correct Answer:
B
To consolidate the two separate firewall policies for Sales and Engineering departments accessing the same web server, you can create an Interface Group that includes both port1 (Sales) and port2 (Engineering). Once the Interface Group is created, you can use this group as a single incoming interface in a single firewall policy. This approach reduces the number of policies, making management more efficient.
References: FortiOS 7.4.1 Administration Guide: Firewall Policy Configuration
FortiOS 7.4.1 Administration Guide: Firewall Policy Configuration
Which of the following methods can be used to configure FortiGate to perform source NAT (SNAT) for outgoing traffic?
Correct Answer:
B
To configure source NAT (SNAT) for outgoing traffic on FortiGate, one of the most common methods
is to enable the "Use Outgoing Interface Address" option in a firewall policy. This option ensures
that the source IP address of packets leaving the FortiGate device is replaced by the IP address of the
outgoing interface. This is typically done when traffic is exiting a private network to access the internet,
requiring source NAT to translate the private IP addresses to a public IP.
Why the other options are less appropriate:
* A. Configure a static route pointing to the external interface: A static route is used to direct
traffic, but it does not configure SNAT. It determines where packets are sent but does not modify
the source IP.
• C. Create a virtual server with an external IP address: Virtual servers are used to provide
destination NAT (DNAT) for incoming traffic, not SNAT for outgoing traffic.
• D. Deploy an IPsec VPN tunnel with NAT enabled: While IPsec VPN tunnels can be configured
with NAT traversal, this is not the typical method for configuring SNAT for general outgoing
internet traffic.
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.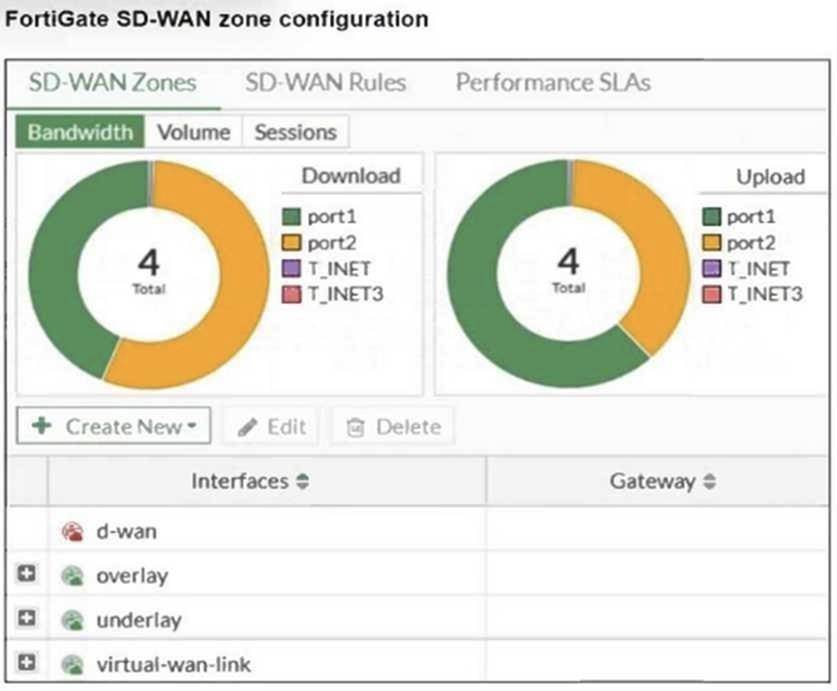
Based on the exhibit, which statement is true?
Correct Answer:
C
In FortiGate's SD-WAN configuration, the d-wan zone is a system default SD-WAN zone that is automatically created and cannot be deleted. This zone is used to manage dynamic WAN links for SD-WAN
traffic balancing and routing. It ensures that multiple WAN interfaces can be grouped and managed
effectively for WAN link optimization.
Why the other options are less appropriate:
• A. The underlay zone contains port1 and: There is no mention in the exhibit about an "underlay zone" containing port1.
• B. The d-wan zone contains no member: This statement is irrelevant since the focus is on the zone's deletion, not its members.
• D. The virtual-wan-link zone contains no member: This is unrelated to the core fact that the d-wan zone cannot be deleted.
Reference:
FortiOS 7.4.1 Administration Guide: SD-WAN Zone Configuration
Which three methods are used by the collector agent for AD polling? (Choose three.)
Correct Answer:
ABC
The Fortinet Single Sign-On (FSSO) Collector Agent supports three primary methods for Active Directory (AD) polling to collect user information: WinSecLog: Monitors Windows Security Event Logs for login events.
WinSecLog: Monitors Windows Security Event Logs for login events. WMI: Uses Windows Management Instrumentation to poll user login sessions.
WMI: Uses Windows Management Instrumentation to poll user login sessions. NetAPI: Utilizes the Netlogon API to query domain controllers for user session data.
NetAPI: Utilizes the Netlogon API to query domain controllers for user session data.
These methods allow the FortiGate to gather user logon information and enforce user-based policies effectively.
References: FortiOS 7.4.1 Administration Guide: FSSO Configuration
FortiOS 7.4.1 Administration Guide: FSSO Configuration