Which two IP pool types are useful for carrier-grade NAT deployments? (Choose two.)
Correct Answer:
AB
In carrier-grade NAT (CGNAT) deployments, specific IP pool types are used to manage large-scale NAT
translations efficiently. The correct IP pool types for CGNAT are:
• A. Port block allocation: This type of IP pool allocates a block of ports from a single public IP to
multiple clients. It allows efficient use of a limited number of public IPs by distributing port ranges
among users, which is crucial for carrier-grade NAT environments where a large number of users
need access to the internet.
• B. Fixed port range: In this type, each client is assigned a fixed range of ports, ensuring that the
same public IP and port range are used consistently. This helps in reducing the complexity and
overhead of managing dynamic port assignments, which is particularly useful in large-scale CGNAT
setups.
Why the other options are less appropriate:
• C. One-to-one: One-to-one NAT is used for mapping a single private IP address to a single public
IP address. This is not efficient for carrier-grade NAT because CGNAT is designed to allow multiple
clients to share a smaller number of public IPs.
• D. Overload: Overload, also known as PAT (Port Address Translation), maps multiple private IPs to
a single public IP by differentiating connections based on port numbers. While commonly used in
regular NAT setups, CGNAT benefits more from port block allocation and fixed port range due to th
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
All traffic must be routed through the primary tunnel when both tunnels are up. The secondary tunnel must be used only if the primary tunnel goes down. In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover.
Which two key configuration changes must the administrator make on FortiGate to meet the requirements? (Choose two.)
Correct Answer:
AC
To configure redundant IPsec VPN tunnels on FortiGate with failover capability, the following two key configuration changes are required: A. Enable Dead Peer Detection (DPD): Dead Peer Detection is crucial for detecting if the remote peer is unreachable. By enabling DPD, FortiGate can quickly detect a dead tunnel, ensuring a faster failover to the secondary tunnel when the primary tunnel goes down.
A. Enable Dead Peer Detection (DPD): Dead Peer Detection is crucial for detecting if the remote peer is unreachable. By enabling DPD, FortiGate can quickly detect a dead tunnel, ensuring a faster failover to the secondary tunnel when the primary tunnel goes down. C. Configure a lower distance on the static route for the primary tunnel and a higher distance on the static route for the secondary tunnel: The static route with the lower distance (higher priority) will be used when both tunnels are operational. If the primary tunnel fails, the higher distance (lower priority) route for the secondary tunnel will take over, ensuring traffic is routed correctly.
C. Configure a lower distance on the static route for the primary tunnel and a higher distance on the static route for the secondary tunnel: The static route with the lower distance (higher priority) will be used when both tunnels are operational. If the primary tunnel fails, the higher distance (lower priority) route for the secondary tunnel will take over, ensuring traffic is routed correctly.
The other options are not suitable: B. Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels:
B. Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels:
This option is not directly related to the requirements of failover between two IPsec VPN tunnels. D. Configure a higher distance on the static route for the primary tunnel and a lower distance on the static route for the secondary tunnel: This would prioritize the secondary tunnel over the primary tunnel, which is opposite to the desired configuration.
D. Configure a higher distance on the static route for the primary tunnel and a lower distance on the static route for the secondary tunnel: This would prioritize the secondary tunnel over the primary tunnel, which is opposite to the desired configuration.
References FortiOS 7.4.1 Administration Guide - Configuring IPsec VPN, page 1320.
FortiOS 7.4.1 Administration Guide - Configuring IPsec VPN, page 1320. FortiOS 7.4.1 Administration Guide - Redundant VPN Configuration, page 1335.
FortiOS 7.4.1 Administration Guide - Redundant VPN Configuration, page 1335.
Refer to the exhibit.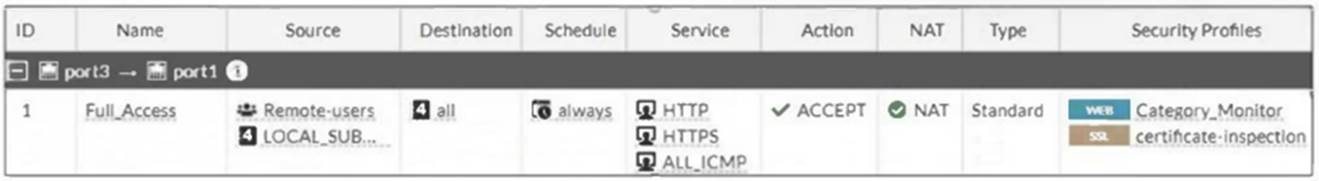
FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt.
What is the most likely reason for this situation?
Correct Answer:
A
Firewall authentication generally requires the DNS service to be enabled in the firewall policy to correctly resolve hostnames during the authentication process. If DNS is not allowed in the firewall policy, the FortiGate cannot resolve external domains, and as a result, the user may not be presented with the login prompt when attempting to access an external website.
References: FortiOS 7.4.1 Administration Guide: Firewall Authentication Configuration
FortiOS 7.4.1 Administration Guide: Firewall Authentication Configuration
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
Correct Answer:
ADE
When FortiGate performs SSL/SSH full inspection and detects an invalid certificate, there are three valid actions it can take: Allow & Warning: This action allows the session but generates a warning.
Allow & Warning: This action allows the session but generates a warning.  Block & Warning: This action blocks the session and generates a warning.
Block & Warning: This action blocks the session and generates a warning.  Block: This action blocks the session without generating a warning.
Block: This action blocks the session without generating a warning.
Actions such as "Trust & Allow" or just "Allow" without additional configurations are not applicable in the context of handling invalid certificates.
References: FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
What is the primary FortiGate election process when the HA override setting is disabled?
Correct Answer:
A
When the HA override setting is disabled, FortiGate uses the primary election process based on the following criteria: Connected monitored ports: The unit with the most monitored ports up is preferred.
Connected monitored ports: The unit with the most monitored ports up is preferred. Priority: The unit with the highest priority is preferred.
Priority: The unit with the highest priority is preferred. System uptime: The unit with the longest uptime is preferred.
System uptime: The unit with the longest uptime is preferred. FortiGate serial number: Used as the final criterion to break any remaining ties.
FortiGate serial number: Used as the final criterion to break any remaining ties.
References: FortiOS 7.4.1 Administration Guide: HA election process
FortiOS 7.4.1 Administration Guide: HA election process