- (Exam Topic 3)
Make Secondary belongs the jeff and marion users on sysusers group. But harold user should not belongs to sysusers group.
Solution:
usermod -G sysusers jeff
usermod -G sysuser marion
Verify by reading /etc/group file Note:
Using usermod command we can make user belongs to different group. There are two types of group one primary and another is secondary. Primary group can be only one but user can belong to more than one group as secondary.
usermod -g groupname username - To change the primary group of the user. usermod -G groupname username
- To make user belongs to secondary group.
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 2)
According to the following requirements, deploy your ftp login rule:
Users in example.com domain must be able to login to your ftp server as an anonymous user.
But users outside the example.com domain are unable to login to your server
Solution: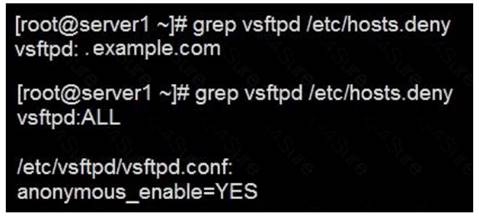
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 3)
Add a cron schedule to take full backup of /home on every day at 5:30 pm to /dev/st0 device.
Solution:
1. vi /var/schedule
30 17 * * * /sbin/dump -0u /dev/st0 /dev/hda7
2. crontab /var/schedule
3. service crond restart
We can add the cron schedule either by specifying the scripts path on /etc/crontab file or by creating on text file on crontab pattern.
cron helps to schedule on recurring events. Pattern of cron is: Minute Hour Day of Month Month Day of Week Commands
0-59 0-23 1-31 1-12 0-7 where 0 and 7 mean Sunday.
Note * means every. To execute the command on every two minutes */2.
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Configure NFS mount.
Mount /nfsshare directory on desktopX under /public directory persistently at system boot time.
Mount /nfssecure/protected with krb5p secured share on desktopX beneath /secure/protected provided with keytab station.network0.example.com/pub/keytabs/desktopX.keytab"> http://station.network0.example.com/pub/keytabs/desktopX.keytab
The user harry is able to write files on /secure directory
Solution: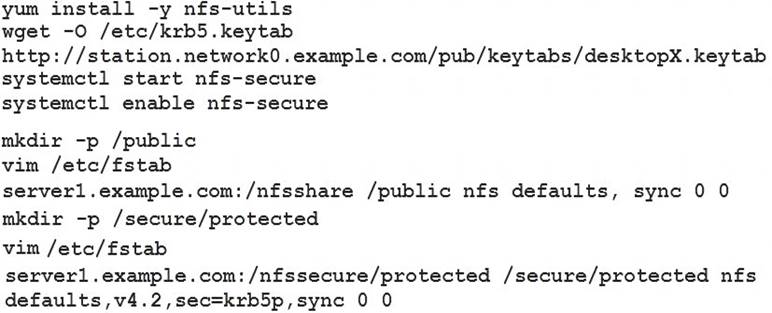
Verification from DesktopX: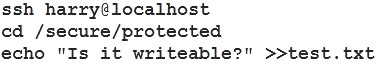
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 2)
In accordance with the following requirements to deploy ssh login service:
harry belongs to example.com which can remote login your systems.
However, users of remote.test cannot use ssh login to your machine.
Solution: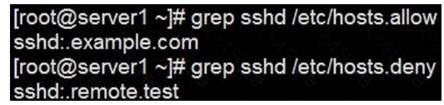
Notice:
tcp_wrappers has two configuration files and their priority level is /etc/hosts.allow->/etc/hosts.deny
Does this meet the goal?
Correct Answer:
A