- (Exam Topic 2)
Create and run an Ansible ad-hoc command.
--> As a system administrator, you will need to install software on the managed nodes.
--> Create a shell script called yum-pack.sh that runs an Ansible ad-hoc command to create yum-repository on each of the managed nodes as follows:
--> repository1
----------
* 1. The name of the repository is EX407
* 2. The description is "Ex407 Description"
* 3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/
* 4. GPG signature checking is enabled
* 5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEYredhat- release
* 6. The repository is enabled
--> repository2
----------
* 1. The name of the repository is EXX407
* 2. The description is "Exx407 Description"
* 3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/AppStream/
* 4. GPG signature checking is enabled
* 5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/ RPM-GPG-KEYredhat- release
* 6. The repository is enabled
Solution:
Solution as:
# pwd
/home/admin/ansible
# vim yum-pack.sh
#!/bin/bash
ansible all -m yum_repository -a 'name=EX407 description="Ex407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/
gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
ansible all -m yum_repository -a 'name=EXX407 description="Exx407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/AppStream/
gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
!wq
# chmod +x yum-pack.sh
# bash yum-pack.sh
# ansible all -m command -a 'yum repolist all'
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 1)
Create the users in the file usersjist.yml file provided. Do this in a playbook called users.yml located at
/home/sandy/ansible. The passwords for these users should be set using the lock.yml file from TASK7. When running the playbook, the lock.yml file should be unlocked with secret.txt file from TASK 7.
All users with the job of 'developer' should be created on the dev hosts, add them to the group devops, their password should be set using the pw_dev variable. Likewise create users with the job of 'manager' on the proxy host and add the users to the group 'managers', their password should be set using the pw_mgr variable.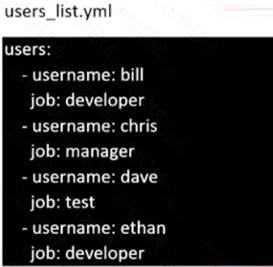
Solution:
ansible-playbook users.yml –vault-password-file=secret.txt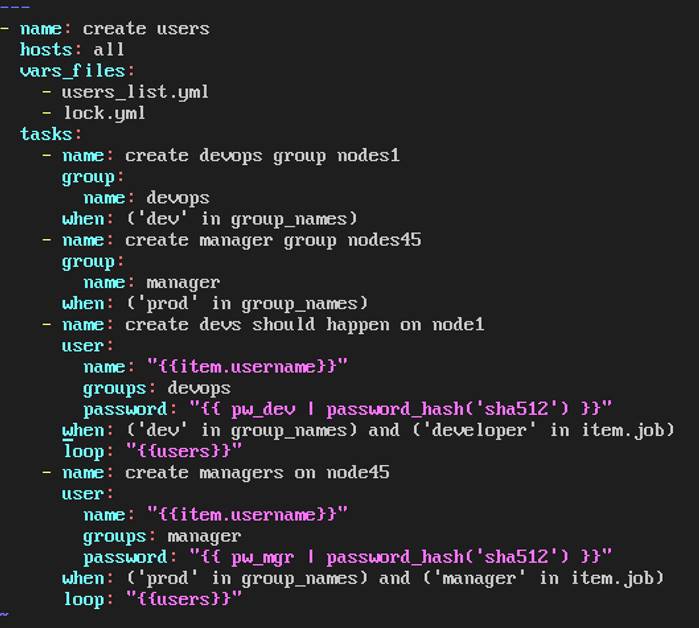
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 1)
Create a jinja template in /home/sandy/ansible/ and name it hosts.j2. Edit this file so it looks like the one below. The order of the nodes doesn't matter. Then create a playbook in /home/sandy/ansible called hosts.yml and install the template on dev node at /root/myhosts
Solution:
Solution as: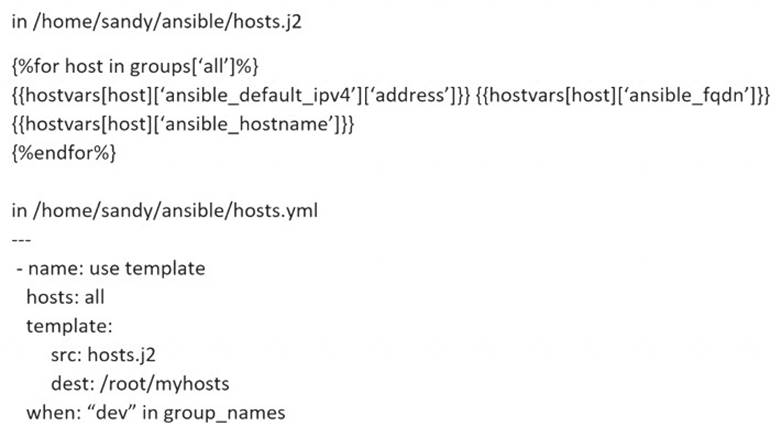
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 2)
Install and configure Ansible on the control-node control.realmX.example.com as follows:
------------------------------------------------------------------------------------------
--> Install the required packages
--> Create a static inventory file called /home/admin/ansible/inventory as follows: node1.realmX.example.com is a member of the dev host group node2.realmX.example.com is a member of the test host group node3.realmX.example.com & node4.realmX.example.com are members of the prod host group
node5.realmX.example.com is a member of the balancers host group. prod group is a member of the webservers host group
--> Create a configuration file called ansible.cfg as follows:
--> The host inventory file /home/admin/ansible/inventory is defined
--> The location of roles used in playbooks is defined as /home/admin/ansible/ roles
Solution:
Solution as:
Through physical host, login to workstation.lab.example.com with user root.
# ssh root@workstation.lab.example.com
# hostname workstation.lab.example.com
# yum install platform-python*
# su - admin
# pwd
/home/admin/
# vim .vimrc
# mkdir -p ansible/roles
# cd ansible
# vim inventory [dev]
servera.lab.example.com [test] serverb.example.com [prod] serverc.example.com serverd.example.com [balancer] serverd.lab.example.com [webservers:children] prod
!wq
# vim ansible.cfg [defaults]
inventory = ./inventory
role_path = ./roles remote_user = admin ask_pass = false [privilege_escalation] become = true become_method = sudo become_user = root become_ask_pass = false
!wq
# ansible all -–list-hosts
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 1)
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in
/home/sandy/ansible/invenlory.
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
Solution:
In/home/sandy/ansible/ansible.cfg
[defaults] inventory=/home/sandy/ansible/inventory roles_path=/home/sandy/ansible/roles remote_user= sandy host_key_checking=false [privilegeescalation]
become=true become_user=root become_method=sudo become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com [test]
[proxy]
node3 .example.com [prod] node4.example.com node5 .example.com [webservers:children] prod
Does this meet the goal?
Correct Answer:
A