Identify the injection attack represented in the diagram below: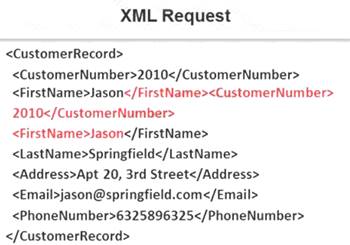
Correct Answer:
C
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
Correct Answer:
C
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set.
What is Terri trying to accomplish by sending this IP packet?
Correct Answer:
C
In the context of penetration testing, what does blue teaming mean?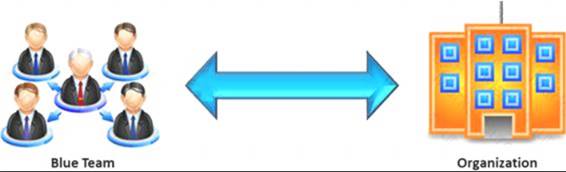
Correct Answer:
A
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
Correct Answer:
A