- (Exam Topic 5)
You have 40 Azure SQL databases, each for a different customer. All the databases reside on the same Azure SQL Database server.
You need to ensure that each customer can only connect to and access their respective database. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Correct Answer:
BE
Manage database access by adding users to the database, or allowing user access with secure connection strings.
Database-level firewall rules only apply to individual databases. Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/database/secure-database-tutorial
- (Exam Topic 5)
You have SQL Server on Azure virtual machines in an availability group. You have a database named DB1 that isNOTin the availability group.
You create a full database backup of DB1.
You need to add DB1 to the availability group.
Which restore option should you use on the secondary replica?
Correct Answer:
B
Prepare a secondary database for an Always On availability group requires two steps:
* 1. Restore a recent database backup of the primary database and subsequent log backups onto each server instance that hosts the secondary replica, using RESTORE WITH NORECOVERY
* 2. Join the restored database to the availability group. Reference:
https://docs.microsoft.com/en-us/sql/database-engine/availability-groups/windows/manually-prepare-asecondary database-for-an-availability-group-sql-server
- (Exam Topic 5)
You have an Azure subscription that contains an Azure Data Factory version 2 (V2) data factory named df1. DF1 contains a linked service.
You have an Azure Key vault named vault1 that contains an encryption kay named key1. You need to encrypt df1 by using key1.
What should you do first?
Correct Answer:
B
A customer-managed key can only be configured on an empty data Factory. The data factory can't contain any resources such as linked services, pipelines and data flows. It is recommended to enable customer-managed key right after factory creation.
Note: Azure Data Factory encrypts data at rest, including entity definitions and any data cached while runs are in progress. By default, data is encrypted with a randomly generated Microsoft-managed key that is uniquely assigned to your data factory.
Reference:
https://docs.microsoft.com/en-us/azure/data-factory/enable-customer-managed-key
- (Exam Topic 5)
You are designing an anomaly detection solution for streaming data from an Azure IoT hub. The solution must meet the following requirements: Send the output to an Azure Synapse.
Send the output to an Azure Synapse. Identify spikes and dips in time series data.
Identify spikes and dips in time series data. Minimize development and configuration effort.
Minimize development and configuration effort.
Which should you include in the solution?
Correct Answer:
C
Anomalies can be identified by routing data via IoT Hub to a built-in ML model in Azure Stream Analytics Reference:
https://docs.microsoft.com/en-us/learn/modules/data-anomaly-detection-using-azure-iot-hub/ https://docs.microsoft.com/en-us/azure/stream-analytics/azure-synapse-analytics-output
- (Exam Topic 5)
You configure a long-term retention policy for an Azure SQL database as shown in the exhibit. (Click the
Exhibit tab.)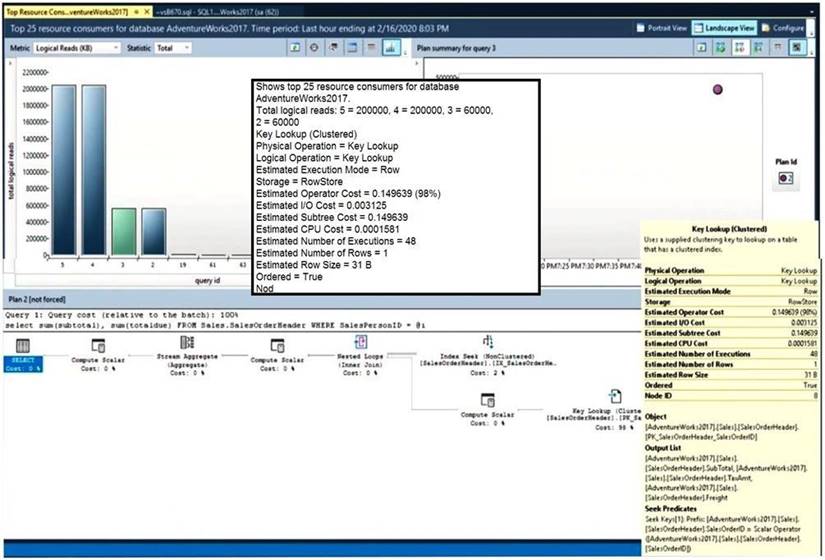
The first weekly backup occurred on January 4, 2020. The dates for the first 10 weekly backups are: January 4, 2020
January 4, 2020 January 11, 2020
January 11, 2020 January 18, 2020
January 18, 2020 January 25, 2020
January 25, 2020 February 1, 2020
February 1, 2020 February 8, 2020
February 8, 2020 February 15, 2020
February 15, 2020 February 22, 2020
February 22, 2020 February 29, 2020
February 29, 2020 March 7, 2020
March 7, 2020
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE:Each correct selection is worth one point.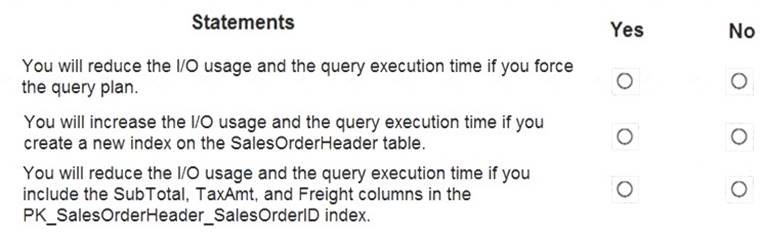
Solution:
Graphical user interface, text, application, email Description automatically generated
Does this meet the goal?
Correct Answer:
A