- (Exam Topic 5)
You have an Azure subscription that contains the resources shown in the following table.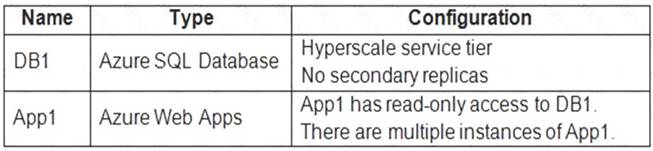
You need to create a read-only replica of DB1 and configure the App1 instances to use the replica. What should you do? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.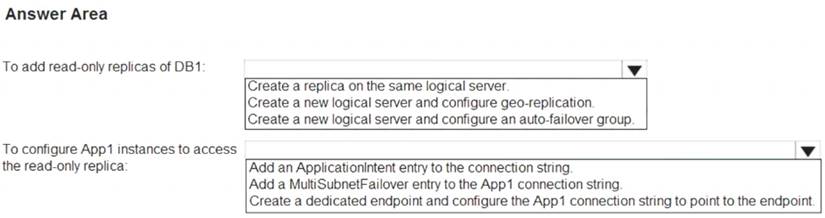
Solution:
Text Description automatically generated
Reference:
https://sqlserverguides.com/read-only-replica-azure-sql/
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 5)
You are building an Azure virtual machine.
You allocate two 1-TiB, P30 premium storage disks to the virtual machine. Each disk provides 5,000 IOPS. You plan to migrate an on-premises instance of Microsoft SQL Server to the virtual machine. The instance has a database that contains a 1.2-TiB data file. The database requires 10,000 IOPS.
You need to configure storage for the virtual machine to support the database.
Which three objects should you create in sequence? To answer, move the appropriate objects from the list of objects to the answer area and arrange them in the correct order.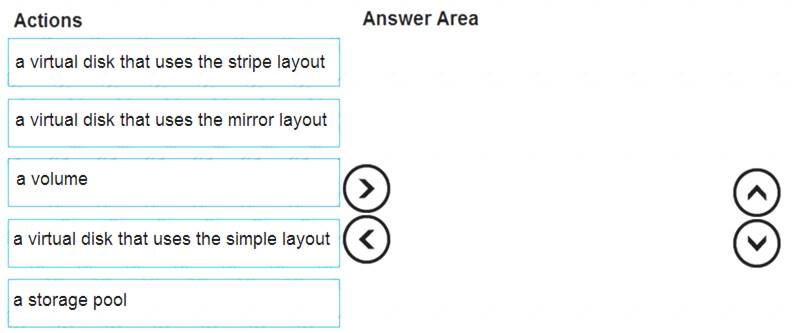
Solution:
Follow these same steps to create striped virtual disk:  Create Log Storage Pool.
Create Log Storage Pool. Create Virtual Disk
Create Virtual Disk  Create Volume
Create Volume
Box 1: a storage pool
Box 2: a virtual disk that uses stripe layout
Disk Striping: Use multiple disks and stripe them together to get a combined higher IOPS and Throughput limit. The combined limit per VM should be higher than the combined limits of attached premium disks.
Box 3: a volume Reference:
https://hanu.com/hanu-how-to-striping-of-disks-for-azure-sql-server/
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 5)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have SQL Server 2019 on an Azure virtual machine.
You are troubleshooting performance issues for a query in a SQL Server instance.
To gather more information, you querysys.dm_exec_requestsand discover that the wait type isPAGELATCH_UPand thewait_resourceis2:3:905856.
You need to improve system performance. Solution: You shrink the transaction log file. Does this meet the goal?
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-US/troubleshoot/sql/performance/recommendations-reduce-allocation-contention
- (Exam Topic 5)
You have an Azure Synapse Analytics dedicated SQL pool named Pool1 and a database named DB1. DB1 contains a fact table named Table.
You need to identify the extent of the data skew in Table1. What should you do in Synapse Studio?
Correct Answer:
D
Use sys.dm_pdw_nodes_db_partition_stats to analyze any skewness in the data. Reference:
https://docs.microsoft.com/en-us/azure/synapse-analytics/sql-data-warehouse/cheat-sheet
- (Exam Topic 5)
You have an Azure SQL database named DB1 in the General Purpose service tier. The performance metrics for DB1 are shown in the following exhibit.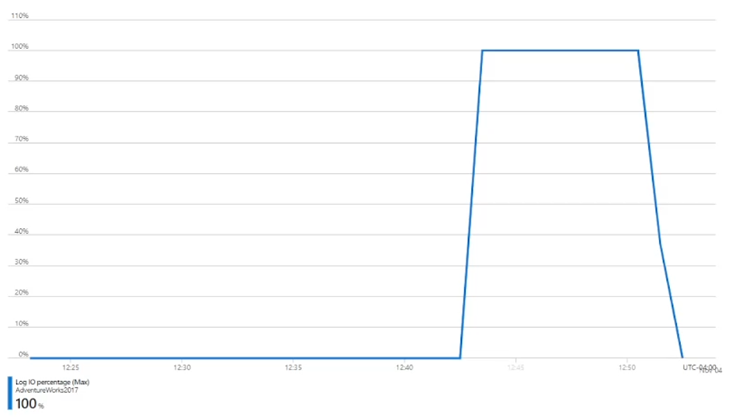
You need to reduce the Log 10 percentage. The solution must minimize costs. What should you do?
Correct Answer:
D