- (Topic 5)
How can a policy help improve an employee's security awareness?
Correct Answer:
A
- (Topic 3)
Jake is a network administrator who needs to get reports from all the computer and network devices on his network. Jake wants to use SNMP but is afraid that won't be secure since passwords and messages are in clear text. How can Jake gather network information in a secure manner?
Correct Answer:
A
- (Topic 7)
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters.
With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
Correct Answer:
D
A dictionary attack will not work as strong passwords are enforced, also the minimum length of 8 characters in the password makes a brute force attack time consuming. A hybrid attack where you take a word from a dictionary and exchange a number of letters with numbers and special characters will probably be the fastest way to crack the passwords.
- (Topic 1)
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR. These flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR = 128
Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.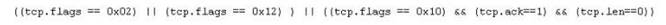
What is Jason trying to accomplish here?
Correct Answer:
B
- (Topic 7)
A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems. However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
Correct Answer:
B
In a Windows 2000 network using Kerberos you normally use pre-
authentication and the user password never leaves the local machine so it is never exposed to the network so it should not be able to be sniffed.