- (Topic 3)
Some passwords are stored using specialized encryption algorithms known as hashes. Why is this an appropriate method?
Correct Answer:
D
- (Topic 2)
What port number is used by LDAP protocol?
Correct Answer:
B
- (Topic 3)
Kevin is an IT security analyst working for Emerson Time Makers, a watch manufacturing company in Miami. Kevin and his girlfriend Katy recently broke up after a big fight. Kevin believes that she was seeing another person. Kevin, who has an online email account that he uses for most of his mail, knows that Katy has an account with that same company. Kevin logs into his email account online and gets the following URL after successfully logged in: http://www.youremailhere.com/mail.asp?mailbox=Kevin&Smith=121%22 Kevin changes the URL to: http://www.youremailhere.com/mail.asp?mailbox=Katy&Sanchez=121%22 Kevin is trying to access her email account to see if he can find out any information. What is Kevin attempting here to gain access to Katy's mailbox?
Correct Answer:
C
- (Topic 1)
What type of Trojan is this?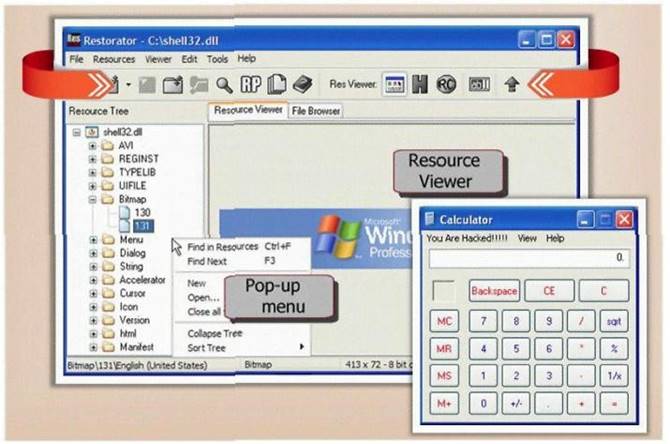
Correct Answer:
C