- (Topic 3)
What is the main reason the use of a stored biometric is vulnerable to an attack?
Correct Answer:
D
- (Topic 7)
Which definition among those given below best describes a covert channel?
Correct Answer:
B
A covert channel is described as: "any communication channel that can be exploited by a process to transfer information in a manner that violates the systems security policy." Essentially, it is a method of communication that is not part of an actual computer system design, but can be used to transfer information to users or system processes that normally would not be allowed access to the information.
- (Topic 4)
The intrusion detection system at a software development company suddenly generates multiple alerts regarding attacks against the company's external webserver, VPN concentrator, and DNS servers. What should the security team do to determine which alerts to check first?
Correct Answer:
C
- (Topic 8)
What type of attack changes its signature and/or payload to avoid detection by antivirus programs?
Correct Answer:
A
In computer terminology, polymorphic code is code that mutates while keeping the original algorithm intact. This technique is sometimes used by computer viruses, shellcodes and computer worms to hide their presence.
- (Topic 1)
How do you defend against DHCP Starvation attack?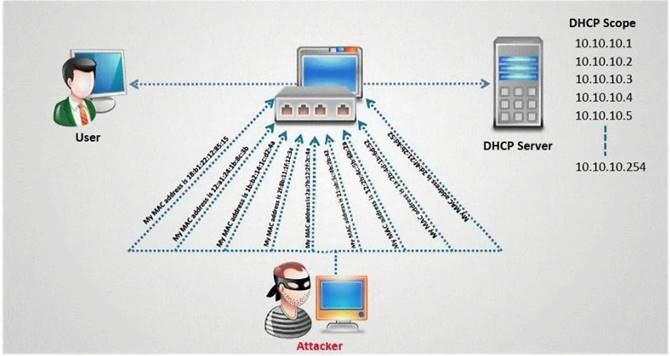
Correct Answer:
B