- (Topic 2)
An Attacker creates a zuckerjournals.com website by copying and mirroring HACKERJOURNALS.COM site to spread the news that Hollywood actor Jason Jenkins died in a car accident. The attacker then submits his fake site for indexing in major search engines. When users search for "Jason Jenkins", attacker's fake site shows up and dupes victims by the fake news.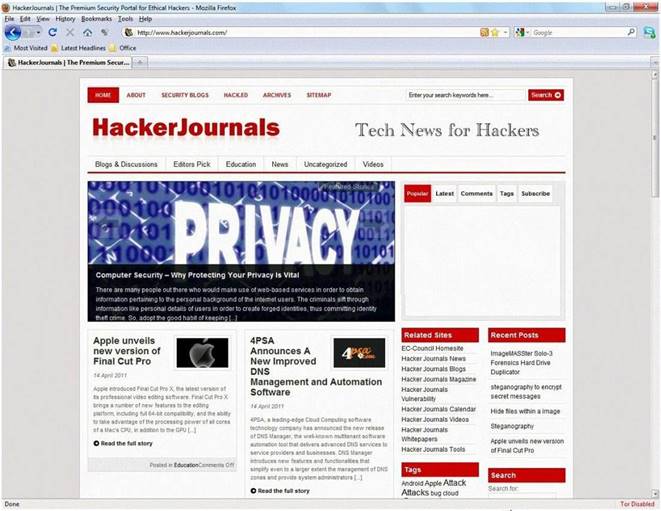
This is another great example that some people do not know what URL's are. Real website:
Fake website: http://www.zuckerjournals.com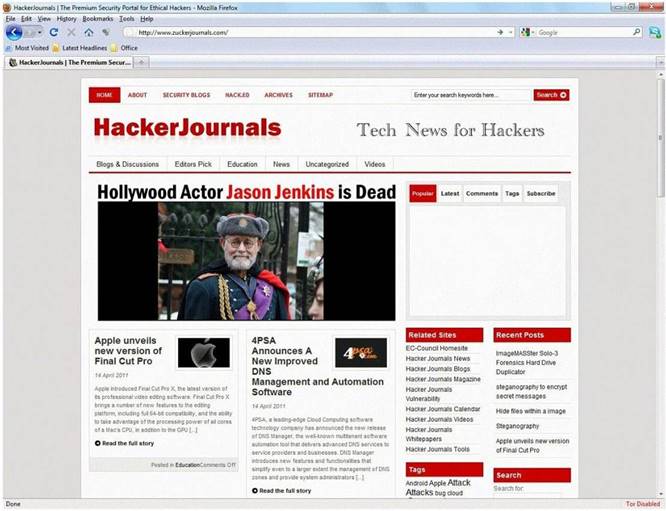
The website is clearly not WWW.HACKERJOURNALS.COM. It is obvious for many, but unfortunately some people still do not know what an URL is. It's the address that you enter into the address bar at the top your browser and this is clearly not legit site, its www.zuckerjournals.com
How would you verify if a website is authentic or not?
Correct Answer:
D
- (Topic 8)
Which of the following wireless technologies can be detected by NetStumbler? (Select all that apply)
Correct Answer:
ACD
If you check the website, cards for all three (A, B, G) are supported. See: http://www.stumbler.net/
- (Topic 7)
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
Correct Answer:
C
All are DDOS tools.
- (Topic 5)
What is the best defense against privilege escalation vulnerability?
Correct Answer:
C
- (Topic 8)
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered. What do you recommend?
Select the best answer.
Correct Answer:
B
Explanations:
Ipchains was improved over ipfwadm with its chaining mechanism so that it can have multiple rulesets. However, it isn't the latest version of a free Linux firewall. Iptables
replaced ipchains and is the latest of the free Linux firewall tools. Any Checkpoint firewall is not going to meet Jason's desire to have a free firewall. Ipfwadm is used to build Linux firewall rules prior to 2.2.0. It is a outdated version.