- (Topic 2)
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server in your organization. They notice that there is excessive number of functions in the source code that might lead to buffer overflow. These C++ functions do not check bounds. Identify the line in the source code that might lead to buffer overflow?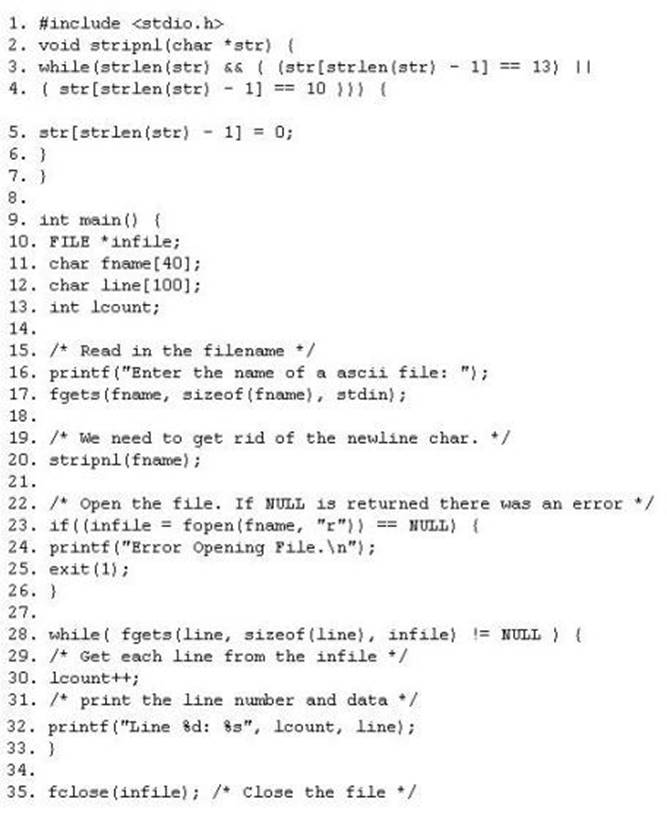
Correct Answer:
B
- (Topic 8)
In an attempt to secure his wireless network, Bob implements a VPN to cover the wireless communications. Immediately after the implementation, users begin complaining about how slow the wireless network is. After benchmarking the network’s speed. Bob discovers that throughput has dropped by almost half even though the number of users has remained the same.
Why does this happen in the VPN over wireless implementation?
Correct Answer:
B
By applying VPN the access point will have to recalculate all headers destined for client and from clients twice.
- (Topic 8)
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
Correct Answer:
B
WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets
bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
- (Topic 4)
Which of the following is an advantage of utilizing security testing methodologies to conduct a security audit?
Correct Answer:
A
- (Topic 3)
If an attacker's computer sends an IPID of 24333 to a zombie (Idle Scanning) computer on
a closed port, what will be the response?
Correct Answer:
A