- (Topic 1)
Bret is a web application administrator and has just read that there are a number of surprisingly common web application vulnerabilities that can be exploited by unsophisticated attackers with easily available tools on the Internet. He has also read that when an organization deploys a web application, they invite the world to send HTTP requests. Attacks buried in these requests sail past firewalls, filters, platform hardening, SSL, and IDS without notice because they are inside legal HTTP requests. Bret is determined to weed out vulnerabilities.
What are some of the common vulnerabilities in web applications that he should be concerned about?
Correct Answer:
A
- (Topic 6)
MX record priority increases as the number increases. (True/False.
Correct Answer:
B
The highest priority MX record has the lowest number.
- (Topic 3)
Low humidity in a data center can cause which of the following problems?
Correct Answer:
C
- (Topic 8)
A program that defends against a port scanner will attempt to:
Correct Answer:
D
- (Topic 6)
You have initiated an active operating system fingerprinting attempt with nmap against a target system: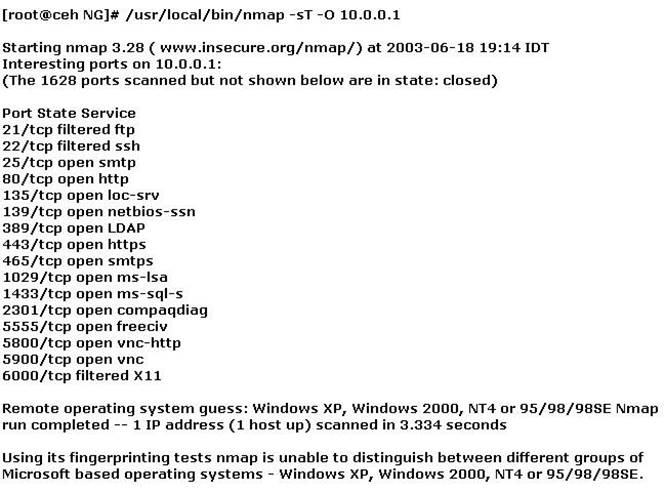
What operating system is the target host running based on the open ports shown above?
Correct Answer:
D
The system is reachable as an active directory domain controller (port 389, LDAP)