- (Topic 2)
The FIN flag is set and sent from host A to host B when host A has no more data to transmit (Closing a TCP connection). This flag releases the connection resources. However, host A can continue to receive data as long as the SYN sequence numbers of transmitted packets from host B are lower than the packet segment containing the set FIN flag.
Correct Answer:
B
- (Topic 8)
If you come across a sheepdip machaine at your client site, what would you infer?
Correct Answer:
A
Also known as a footbath, a sheepdip is the process of checking physical media, such as floppy disks or CD-ROMs, for viruses before they are used in a computer. Typically, a computer that sheepdips is used only for that process and nothing else and is isolated from the other computers, meaning it is not connected to the network. Most sheepdips use at least two different antivirus programs in order to increase effectiveness.
- (Topic 8)
Jim is having no luck performing a penetration test in XYZ’s network. He is running the tests from home and has downloaded every security scanner that he could lay his hands on. Despite knowing the IP range of all the systems, and the exact network configuration, Jim is unable to get any useful results.
Why is Jim having these problems?
Correct Answer:
D
The Security scanners available online are often to “outdated” to perform a live pentest against a victim.
- (Topic 7)
Exhibit: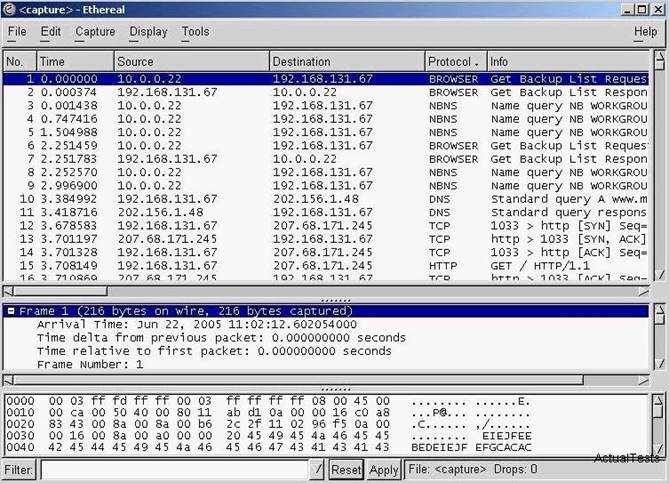
You have captured some packets in Ethereal. You want to view only packets sent from
10.0.0.22. What filter will you apply?
Correct Answer:
B
ip.src tells the filter to only show packets with 10.0.0.22 as the source.
- (Topic 4)
Which initial procedure should an ethical hacker perform after being brought into an organization?
Correct Answer:
C