- (Topic 7)
Under what conditions does a secondary name server request a zone transfer from a primary name server?
Correct Answer:
A
Understanding DNS is critical to meeting the requirements of the CEH. When the serial number that is within the SOA record of the primary server is higher than the Serial number within the SOA record of the secondary DNS server, a zone transfer will take place.
- (Topic 8)
John is using tokens for the purpose of strong authentication. He is not confident that his security is considerably strong.
In the context of Session hijacking why would you consider this as a false sense of security?
Correct Answer:
B
A token will give you a more secure authentication, but the tokens will not help against attacks that are directed against you after you have been authenticated.
- (Topic 2)
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company's network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place. Your peer, Peter Smith who works at the same department disagrees with you. He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of "weakest link" in the security chain. What is Peter Smith talking about?
Correct Answer:
A
- (Topic 1)
Which type of scan does NOT open a full TCP connection?
Correct Answer:
A
- (Topic 8)
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe.
What caused this?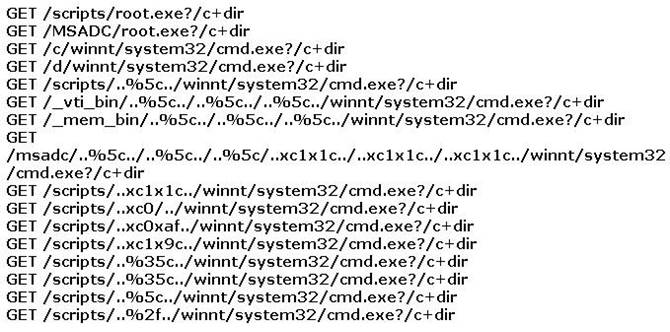
Correct Answer:
D
The Nimda worm modifies all web content files it finds. As a result, any user browsing web content on the system, whether via the file system or via a web server, may download a copy of the worm. Some browsers may automatically execute the downloaded copy, thereby, infecting the browsing system. The high scanning rate of the Nimda worm may also cause bandwidth denial-of-service conditions on networks with infected machines and allow intruders the ability to execute arbitrary commands within the Local System security context on machines running the unpatched versions of IIS.