HOTSPOT - (Topic 8)
You are developing a solution that uses the Azure Storage Client library for .NET. You have the following code: (Line numbers are included for reference only.)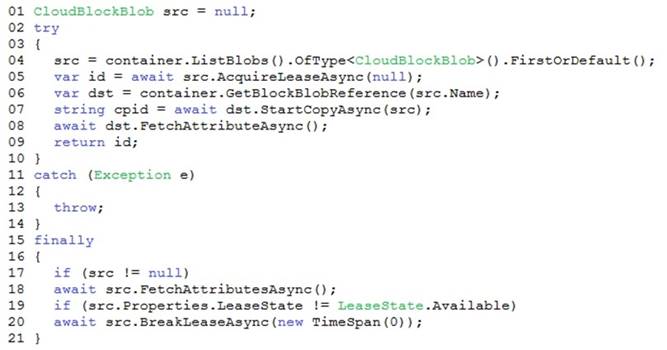
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.
Solution:
Box 1: Yes
AcquireLeaseAsync does not specify leaseTime.
leaseTime is a TimeSpan representing the span of time for which to acquire the lease, which will be rounded down to seconds. If null, an infinite lease will be acquired. If not null, this must be 15 to 60 seconds.
Box 2: No
The GetBlockBlobReference method just gets a reference to a block blob in this container.
Box 3: Yes
The BreakLeaseAsync method initiates an asynchronous operation that breaks the current lease on this container.
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 8)
A company is developing a gaming platform. Users can join teams to play online and see leaderboards that include player statistics. The solution includes an entity named Team.
You plan to implement an Azure Redis Cache instance to improve the efficiency of data operations for entities that rarely change.
You need to invalidate the cache when team data is changed.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.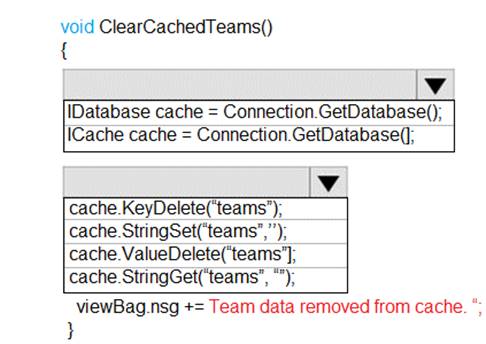
Solution:
Box 1: IDatabase cache = connection.GetDatabase();
Connection refers to a previously configured ConnectionMultiplexer.
Box 2: cache.StringSet("teams",")
To specify the expiration of an item in the cache, use the TimeSpan parameter of
StringSet.
cache.StringSet("key1", "value1", TimeSpan.FromMinutes(90));
References:
https://azure.microsoft.com/sv-se/blog/lap-around-azure-redis-cache-preview/
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 8)
You are developing a web application that makes calls to the Microsoft Graph API. You register the application in the Azure portal and upload a valid X509 certificate.
You create an appsettings.json file containing the certificate name, client identifier for the application, and the tenant identifier of the Azure active Directory (Azure AD). You create a method named ReadCertificate to return the X509 certificate by name.
You need to implement code that acquires a token by using the certificate.
How should you complete the code segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.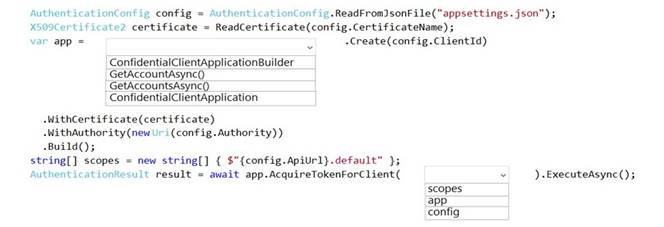
Solution:
https://docs.microsoft.com/en-us/azure/active-directory/develop/scenario-daemon-app-configuration?tabs=dotnet#instantiate-the-confidential-client-application-with-a-client- certificate
https://docs.microsoft.com/en-us/azure/active-directory/develop/scenario-daemon-acquire-token?tabs=dotnet#acquiretokenforclient-api
Does this meet the goal?
Correct Answer:
A
DRAG DROP - (Topic 8)
You are a developer for a software as a service (SaaS) company that uses an Azure Function to process orders. The Azure Function currently runs on an Azure Function app that is triggered by an Azure Storage queue.
You are preparing to migrate the Azure Function to Kubernetes using Kubernetes-based Event Driven Autoscaling (KEDA).
You need to configure Kubernetes Custom Resource Definitions (CRD) for the Azure Function.
Which CRDs should you configure? To answer, drag the appropriate CRD types to the correct locations. Each CRD type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE:Each correct selection is worth one point.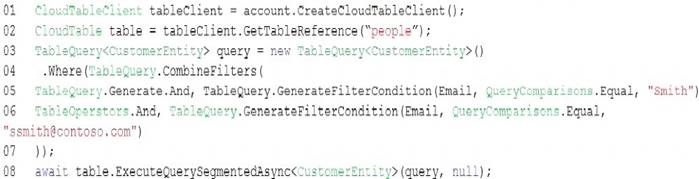
Solution:
Box 1: Deployment
To deploy Azure Functions to Kubernetes use the func kubernetes deploy command has several attributes that directly control how our app scales, once it is deployed to Kubernetes.
Box 2: ScaledObject
With --polling-interval, we can control the interval used by KEDA to check Azure Service
Bus Queue for messages.
Example of ScaledObject with polling interval apiVersion: keda.k8s.io/v1alpha1
kind: ScaledObject metadata:
name: transformer-fn namespace: tt labels:
deploymentName: transformer-fn spec:
scaleTargetRef: deploymentName: transformer-fn pollingInterval: 5
minReplicaCount: 0
maxReplicaCount: 100
Box 3: Secret
Store connection strings in Kubernetes Secrets. Example: to create the Secret in our demo Namespace:
# create the k8s demo namespace kubectl create namespace tt
# grab connection string from Azure Service Bus KEDA_SCALER_CONNECTION_STRING=$(az servicebus queue authorization-rule keys list
-g $RG_NAME
--namespace-name $SBN_NAME
--queue-name inbound
-n keda-scaler
--query "primaryConnectionString"
-o tsv)
# create the kubernetes secret
kubectl create secret generic tt-keda-auth
--from-literal KedaScaler=$KEDA_SCALER_CONNECTION_STRING
--namespace tt
Does this meet the goal?
Correct Answer:
A
DRAG DROP - (Topic 8)
Your company has several websites that use a company logo image. You use Azure Content Delivery Network (CDN) to store the static image.
You need to determine the correct process of how the CDN and the Point of Presence (POP) server will distribute the image and list the items in the correct order.
In which order do the actions occur? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Solution:
Step 1: A user requests the image..
A user requests a file (also called an asset) by using a URL with a special domain name, such as
Step 2: If no edge servers in the POP have the..
If no edge servers in the POP have the file in their cache, the POP requests the file from the origin server. The origin server can be an Azure Web App, Azure Cloud Service, Azure Storage account, or any publicly accessible web server.
Step 3: The origin server returns the..
The origin server returns the file to an edge server in the POP.
An edge server in the POP caches the file and returns the file to the original requestor (Alice). The file remains cached on the edge server in the POP until the time-to-live (TTL) specified by its HTTP headers expires. If the origin server didn't specify a TTL, the default TTL is seven days.
Step 4: Subsequent requests for..
Additional users can then request the same file by using the same URL that the original user used, and can also be directed to the same POP.
If the TTL for the file hasn't expired, the POP edge server returns the file directly from the cache. This process results in a faster, more responsive user experience.
References:
https://docs.microsoft.com/en-us/azure/cdn/cdn-overview
Does this meet the goal?
Correct Answer:
A