HOTSPOT - (Topic 8)
You are developing an application that use an Azure blob named data to store application data. The application creates blob snapshots to allow application state to be reverted to an earlier state. The Azure storage account has soft deleted enabled.
The system performs the following operations in order:
•The blob is updated
•Snapshot 1 is created.
•Snapshot 2 is created.
•Snapshot 1 is deleted.
A system error then deletes the data blob and all snapshots.
You need to determine which application states can be restored.
What is the restorability of the application data? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.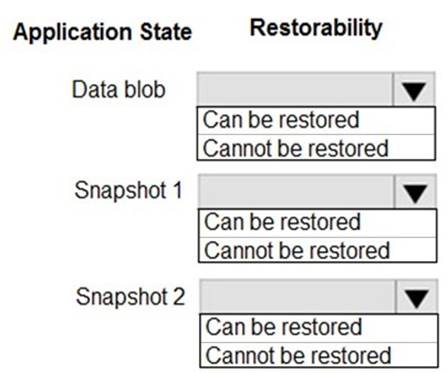
Solution:
Box 1: Can be restored
When enabled, soft delete enables you to save and recover your data when blobs or blob snapshots are deleted. This protection extends to blob data that is erased as the result of an overwrite.
Box 2: Cannot be restored It has been deleted.
Box 3: Can be restored It has not been deleted.
References:
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-soft-delete
Does this meet the goal?
Correct Answer:
A
DRAG DROP - (Topic 8)
You are developing Azure WebJobs.
You need to recommend a WebJob type for each scenario.
Which WebJob type should you recommend? To answer, drag the appropriate WebJob types to the correct scenarios. Each WebJob type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE:Each correct selection is worth one point.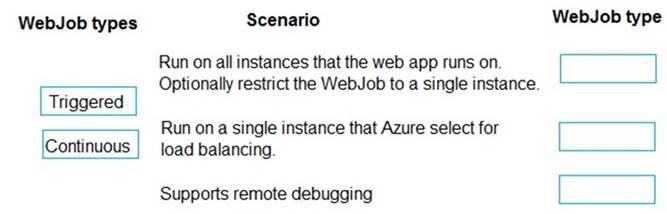
Solution:
Box 1: Continuous
Continuous runs on all instances that the web app runs on. You can optionally restrict the WebJob to a single instance.
Box 2: Triggered
Triggered runs on a single instance that Azure selects for load balancing.
Box 3: Continuous
Continuous supports remote debugging.
Note:
The following table describes the differences between continuous and triggered WebJobs.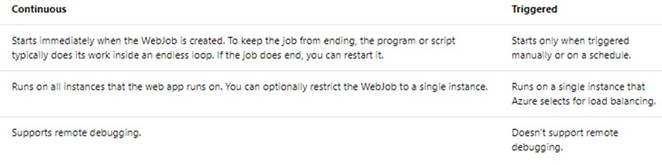
References:
https://docs.microsoft.com/en-us/azure/app-service/web-sites-create-web-jobs
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 8)
You are configuring a new development environment for a Java application.
The environment requires a Virtual Machine Scale Set (VMSS), several storage accounts, and networking components.
The VMSS must not be created until the storage accounts have been successfully created and an associated load balancer and virtual network is configured.
How should you complete the Azure Resource Manager template? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
Solution:
Box 1: copyIndex
Notice that the name of each resource includes the copyIndex() function, which returns the current iteration in the loop. copyIndex() is zero-based.
Box 2: copy
By adding the copy element to the resources section of your template, you can dynamically set the number of resources to deploy.
Box 3: dependsOn Example:
"type": "Microsoft.Compute/virtualMachineScaleSets", "apiVersion": "2020-06-01",
"name": "[variables('namingInfix')]",
"location": "[parameters('location')]", "sku": {
"name": "[parameters('vmSku')]", "tier": "Standard",
"capacity": "[parameters('instanceCount')]"
},
"dependsOn": [
"[resourceId('Microsoft.Network/loadBalancers', variables('loadBalancerName'))]", "[resourceId('Microsoft.Network/virtualNetworks', variables('virtualNetworkName'))]"
],
Does this meet the goal?
Correct Answer:
A
DRAG DROP - (Topic 8)
You are developing a serverless Java application on Azure. You create a new Azure Key Vault to work with secrets from a new Azure Functions application.
The application must meet the following requirements:
✑ Reference the Azure Key Vault without requiring any changes to the Java code.
✑ Dynamically add and remove instances of the Azure Functions host based on the number of incoming application events.
✑ Ensure that instances are perpetually warm to avoid any cold starts.
✑ Connect to a VNet.
✑ Authentication to the Azure Key Vault instance must be removed if the Azure Function application is deleted.
You need to grant the Azure Functions application access to the Azure Key Vault.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.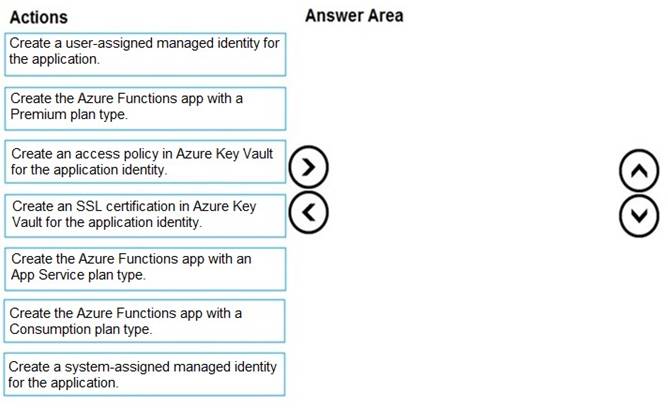
Solution:
Step 1: Create the Azure Functions app with a Consumption plan type. Use the Consumption plan for serverless.
Step 2: Create a system-assigned managed identity for the application. Create a system-assigned managed identity for your application.
Key Vault references currently only support system-assigned managed identities. User- assigned identities cannot be used.
Step 3: Create an access policy in Key Vault for the application identity.
Create an access policy in Key Vault for the application identity you created earlier. Enable the "Get" secret permission on this policy. Do not configure the "authorized application" or
applicationId settings, as this is not compatible with a managed identity.
Does this meet the goal?
Correct Answer:
A
- (Topic 8)
You are developing a user portal for a company.
You need to create a report for the portal that lists information about employees who are subject matter experts for a specific topic. You must ensure that administrators have full control and cosent over the data.
Which technology should you use?
Correct Answer:
C