HOTSPOT - (Topic 8)
A software as a service (SaaS) company provides document management services. The company has a service that consists of several Azure web apps. All Azure web apps run in an Azure App Service Plan named PrimaryASP.
You are developing a new web service by using a web app named ExcelParser. The web app contains a third-party library for processing Microsoft Excel files. The license for the third-party library stipulates that you can only run a single instance of the library.
You need to configure the service.
How should you complete the script? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.
Solution: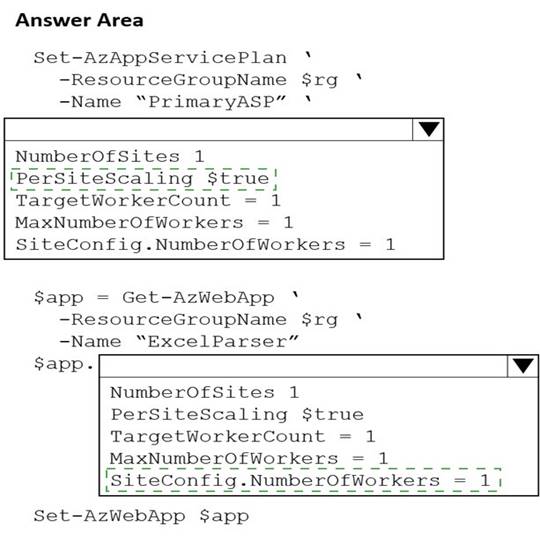
Does this meet the goal?
Correct Answer:
A
- (Topic 5)
You need to resolve the capacity issue. What should you do?
Correct Answer:
D
If you want to read the files in parallel, you cannot use forEach. Each of the async callback function calls does return a promise. You can await the array of promises that you'll get with Promise.all.
Scenario: Capacity issue: During busy periods, employees report long delays between the time they upload the receipt and when it appears in the web application.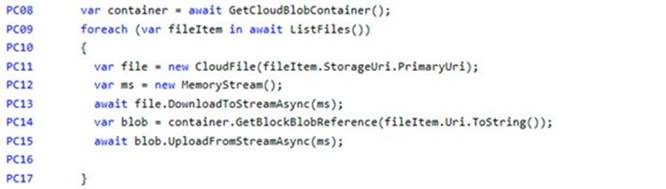
Reference:
https://stackoverflow.com/questions/37576685/using-async-await-with-a-foreach-loop
- (Topic 8)
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing an Azure Service application that processes queue data when it receives a message from a mobile application. Messages may not be sent to the service consistently.
You have the following requirements:
✑ Queue size must not grow larger than 80 gigabytes (GB).
✑ Use first-in-first-out (FIFO) ordering of messages.
✑ Minimize Azure costs.
You need to implement the messaging solution.
Solution: Use the .Net API to add a message to an Azure Storage Queue from the mobile application. Create an Azure VM that is triggered from Azure Storage Queue events.
Does the solution meet the goal?
Correct Answer:
B
Don't use a VM, instead create an Azure Function App that uses an Azure Service Bus Queue trigger.
Reference:
https://docs.microsoft.com/en-us/azure/azure-functions/functions-create-storage-queue- triggered-function
- (Topic 8)
You deploy an API to API Management
You must secure all operations on the API by using a client certificate.
You need to secure access to the backend service of the API by using client certificates. Which two security features can you use?
Correct Answer:
BC
HOTSPOT - (Topic 8)
You are debugging an application that is running on Azure Kubernetes cluster named cluster1. The cluster uses Azure Monitor for containers to monitor the cluster.
The application has sticky sessions enabled on the ingress controller.
Some customers report a large number of errors in the application over the last 24 hours. You need to determine on which virtual machines (VMs) the errors are occurring.
How should you complete the Azure Monitor query? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.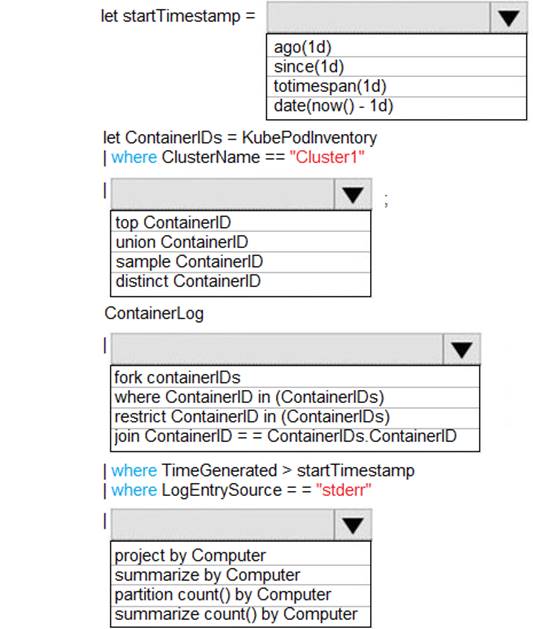
Solution:
Box 1: ago(1d)
Box 2: distinct containerID
Box 3: where ContainerID in (ContainerIDs)
Box 4: summarize Count by Computer Summarize: aggregate groups of rows
Use summarize to identify groups of records, according to one or more columns, and apply aggregations to them. The most common use of summarize is count, which returns the number of results in each group.
Does this meet the goal?
Correct Answer:
A