HOTSPOT - (Topic 5)
You have an Azure subscription.
You plan to create a role definition to meet the following requirements:
• Users must be able to view the configuration data of a storage account.
• Users must be able to perform all actions on a virtual network.
• The solution must use the principle of least privilege.
What should you include in the role definition for each requirement? To answer, select the appropriate options in the answer area.
Solution:
Perform all actions on a virtual network: “Microsoft.Network/virtualNetworks/*”
View the configuration data of a storage account: “Microsoft.Storage/StorageAccounts/read”
To perform all actions on a virtual network, you need to use the wildcard () character in the action string, which grants access to all actions that match the string. The action string for virtual networks is "Microsoft.Network/virtualNetworks/". To view the configuration data of a storage account, you need to use the read action substring in the action string, which enables read actions (GET). The action string for storage accounts is “Microsoft.Storage/StorageAccounts/read”. References:
✑ https://learn.microsoft.com/en-us/azure/role-based-access-control/role-definitions
✑ https://learn.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 5)
You have an Azure subscription that contains the resources shown in the following table.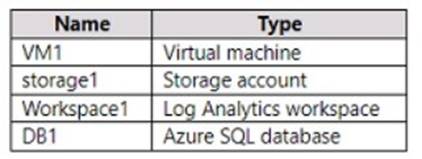
You plan to create a data collection rule named DCRI in Azure Monitor.
Which resources can you set as data sources in DCRI, and which resources can you set as destinations in DCRI? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.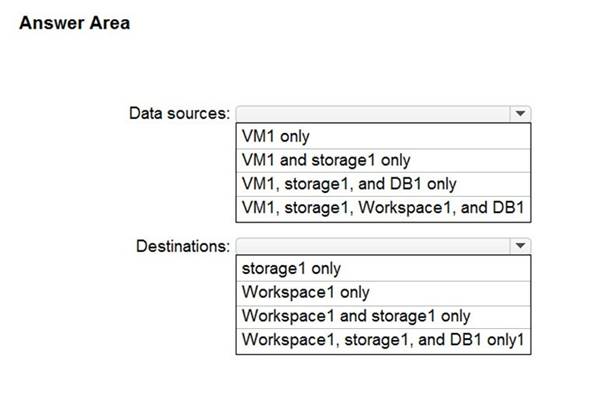
 Answer:
Answer: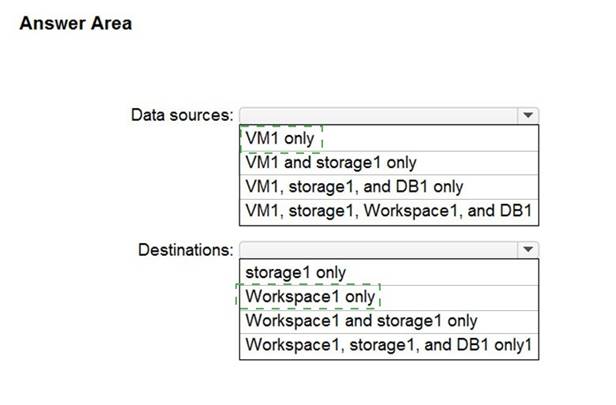
Solution:
Data Sources: VM1 only Destination: Workspace1 Only
Does this meet the goal?
Correct Answer:
A
- (Topic 5)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You create a resource lock, and then you assign the lock to the subscription. Does this meet the goal?
Does this meet the goal?
Correct Answer:
B
No, this does not meet the goal. Creating a resource lock and assigning it to the subscription is not enough to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks. This is because a resource lock does not affect the configuration or functionality of a resource, but only prevents it from being deleted or modified1. A resource lock does not apply any security rules to an NSG or a virtual network.
To meet the goal, you need to create a custom policy definition that enforces a default security rule for NSGs. A policy definition is a set of rules and actions that Azure performs when evaluating your resources2. You can use a policy definition to specify the required properties and values for NSGs, such as the direction, protocol, source, destination, and port of the security rule. You can then assign the policy definition to the subscription scope, so that it applies to all the resource groups and virtual networks in the subscription.
- (Topic 5)
You have an Azure subscription that contains a storage account named storage. You have the devices shown in the following table.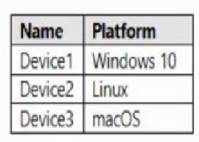
From which devices can you use AzCopy to copy data to storage1?
Correct Answer:
B
https://learn.microsoft.com/en-us/azure/storage/common/storage-use-azcopy- v10#download-azcopy
- (Topic 5)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.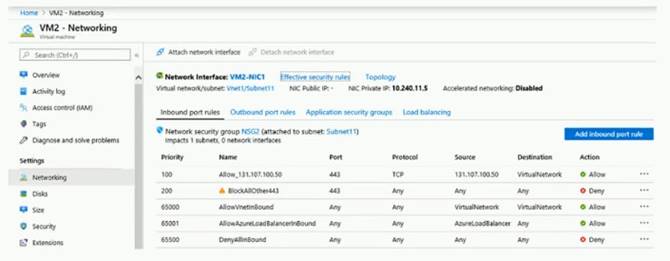
You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail. You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You create an inbound security rule that denies all traffic from the 131.107.100.50 source and has a cost of 64999.
Does this meet the goal?
Correct Answer:
B